Заглавная страница Избранные статьи Случайная статья Познавательные статьи Новые добавления Обратная связь FAQ Написать работу КАТЕГОРИИ: ТОП 10 на сайте Приготовление дезинфицирующих растворов различной концентрацииТехника нижней прямой подачи мяча. Франко-прусская война (причины и последствия) Организация работы процедурного кабинета Смысловое и механическое запоминание, их место и роль в усвоении знаний Коммуникативные барьеры и пути их преодоления Обработка изделий медицинского назначения многократного применения Образцы текста публицистического стиля Четыре типа изменения баланса Задачи с ответами для Всероссийской олимпиады по праву 
Мы поможем в написании ваших работ! ЗНАЕТЕ ЛИ ВЫ?
Влияние общества на человека
Приготовление дезинфицирующих растворов различной концентрации Практические работы по географии для 6 класса Организация работы процедурного кабинета Изменения в неживой природе осенью Уборка процедурного кабинета Сольфеджио. Все правила по сольфеджио Балочные системы. Определение реакций опор и моментов защемления |
Authorship analysis in cybercrime investigationСодержание книги
Поиск на нашем сайте
The development of networking (технологий), and the Internet in particular, has created a new way to share (информацию) across (время и пространство). While computer (сети) have enhanced (качество жизни) in many aspects, they have also opened a (новую сферу криминальной деятельности). These activities have spawned the (понятие) of cybercrime, which (относится) to illegal computer-mediated activities that can be conducted through (всемирные электронные сети), such as the Internet. One predominant type of cybercrime is distribution of (нелегальных материалов) in cyber space. Such materials include pirate software, (детская порнография), stolen properties, etc. Cyber criminals have been using various Web-based (каналы, чтобы распространять) illegal materials such as Email, websites, Internet newsgroups, Internet chat rooms, etc. One common characteristic of these channels is (анонимность). People usually do not need to provide their real identity information, such as (имя, возраст, пол и адрес), in order to participate in cyber activities. Compared to conventional (преступлениями), cybercrime conducted through such (анонимные каналы) imposes unique challenges for law enforcement agencies in criminal identity tracing. The situation is further (осложняется) by the sheer amount of cyber (пользователей) and activities, making the manual approach to criminal identity tracing impossible for meeting cybercrime investigation requirements.
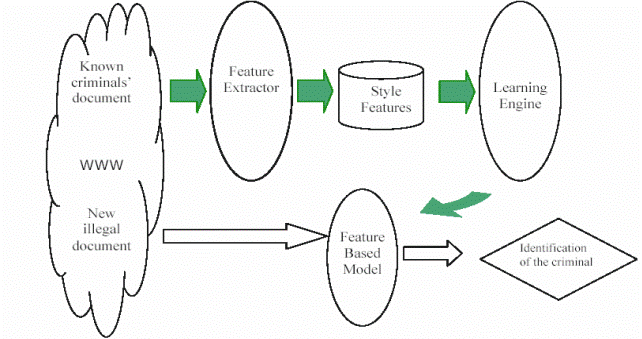
7. Проектная работа. «Applying Authorship Analysis in Cybercrime Investigation». ПРОЕКТ – это «пять П»: проблема, планирование, поиск информации, продукт, презентация. Группа делится на несколько подгрупп (по 4 -5 человек), каждый студент получает самостоятельный участок работы в проекте. Ознакомьтесь с материалом, предложенным ниже, распределите роли, кто, за что будет отвечать, кто выступит с презентацией, кто подберет дополнительный материал по теме, кто подготовит наглядные материалы и т.п. The large amount of cyber space activities and their anonymous nature make cybercrime investigation extremely difficult. One of the major tasks in cybercrime investigation is tracing the real identity source of an illegal document. Normally the investigator tries to attribute a new illegal message to a particular criminal in order to get some new clues. Conventional ways to deal with this problem rely on manual work, which is largely limited by the sheer amount of messages and constantly changing author IDs. Automatic authorship analysis should be highly valuable to cybercrime investigators. Figure 1 depicts the typical process of cybercrime identity tracing using the authorship analysis approach.
Fig. 1 Fig. 1. A Framework of Cybercrime Investigation with Authorship Analysis assumes that an investigator has a collection of illegal documents created by a particular suspected cyber criminal. In the first step the feature extractor runs on those documents and generates a set of style features, which will be used as the input to/for the learning engine. A feature-based model is then created as the outcome of the learning engine. This model can identify whether a newly found illegal document is written by that suspicious criminal under different IDs or names. This information will help the investigator focus his/her effort on a small scope of illegal documents and effectively keep track of more important cyber criminals. Cyberspace texts have several characteristics which are different from those of literary works or published articles and make authorship analysis in cyber space a challenge to researchers. One big problem is that cyber documents are generally short in length. This means that many language-based features successfully used in previous studies may not be appropriate (e.g., vocabulary richness).
Through observation we were able to spot illegal sales of pirate software in all three newsgroups. Figure 2 is an example of such a message.
Fig. 2. Illegal Internet Newsgroup Message
We then identified the 9 most active users (represented by a unique ID and email address) who frequently posted messages in these newsgroups. Messages posted by these users were carefully checked to determine whether or not they indicated illegal activities. Between 8 and 30 illegal messages per user were downloaded for use in the experiment. 8. Прочитайте текст. Составьте план текста и озаглавьте его.
TEXT (Title)_________________________________________________ 1._________________________________________________________________________ a)_____________________________________________________________ b)_____________________________________________________________ c)_____________________________________________________________ d) _____________________________________________________________ e) _____________________________________________________________ 2._________________________________________________________________________ 3. _________________________________________________________________________ 4. _________________________________________________________________________ Forensic linguists are involved in many areas that relate to crime, both solving crime and absolving people wrongly accused of committing crimes. Some of these areas of research include:
ü voice identification (for instance, determining whether the voice on a threatening tape recording was that of the defendant; sometimes also called forensic phonetics);
ü author identification (determining who wrote a particular text by comparing it to known writing samples of a suspect; sometimes also called forensic stylistics);
ü discourse analysis (analyzing the structure of a writing or spoken utterance, often recorded, to help determine issues such as who is introducing topics or whether a suspect is agreeing to engage in a criminal conspiracy);
ü linguistic proficiency (did a suspect understand the Miranda warning or police caution?);
ü dialectology (determining which dialect of a language a person speaks, usually to show that a defendant has a different dialect from that on an incriminating tape recording. As opposed to voice identification, which analyzes the acoustic qualities of the voice, dialectology uses linguistic features to accomplish similar goals).
Author identification is a very interesting and potentially useful area, but it is hampered by the fact that documents in a forensic setting (ransom notes, threatening letters, etc.) are usually much too short to make a reliable identification. Moreover, which linguistic features are reliable indicators of authorship, and how reliable those features are, remains to be discovered. Research is ongoing, however, and the availability of large corpora of speech and writing samples suggests that the field may advance in the future (although the typically small size of the documents in most criminal cases will always be a problem). Moreover, it may be sufficiently reliable to eliminate someone as an author, or select an author from a small group of suspects. Discourse analysis is a very broad field, and how acceptable its conclusions are depends on the methodology that is used and how any conclusions are described. Discourse analysist can provide helpful information by close analysis of a covert recording and, for instance, showing that the suspect's use of "I" rather than "we" might indicate noncomplicity in a conspiracy. Linguists have also pointed out that when a suspect is recorded as saying "yeah" or "uh-huh" in response to a suggestion, the suspect is not necessarily agreeing with the suggestion, but may simply be providing a feedback marker to indicate he has understood the utterance, as we routinely do in ordinary conversation. Courts have a mixed record in whether they allow discourse analysists to testify as experts, but even when not allowed to testify they may be useful to the lawyers in preparing a case. Proficiency testing and dialectology are both time-tested and relatively noncontroversial areas of linguistics. Of course, because of the influence of mass media and population mobility, dialects are becoming less distinct than they once were, and people often mix dialect features. This is a serious problem with linguistic origin analysis. Determining a person's origin by means of his or her dialect or language is also complicated by the fact that many languages straddle a border or are spoken in multiple countries. (by Peter Tiersma, PhD, University of California) 9. Ответьте на вопросы. 1. What do forensic linguists deal with? 2. What type of research do they perform? 3. What are the main difficulties in author identification? 4. What does discourse analysis depend on? 5. Why are proficiency testing and dialectology noncontroversial areas of linguistics?
|
||||
|
Последнее изменение этой страницы: 2016-06-26; просмотров: 321; Нарушение авторского права страницы; Мы поможем в написании вашей работы! infopedia.su Все материалы представленные на сайте исключительно с целью ознакомления читателями и не преследуют коммерческих целей или нарушение авторских прав. Обратная связь - 3.15.26.231 (0.006 с.) |