Заглавная страница Избранные статьи Случайная статья Познавательные статьи Новые добавления Обратная связь FAQ Написать работу КАТЕГОРИИ: ТОП 10 на сайте Приготовление дезинфицирующих растворов различной концентрацииТехника нижней прямой подачи мяча. Франко-прусская война (причины и последствия) Организация работы процедурного кабинета Смысловое и механическое запоминание, их место и роль в усвоении знаний Коммуникативные барьеры и пути их преодоления Обработка изделий медицинского назначения многократного применения Образцы текста публицистического стиля Четыре типа изменения баланса Задачи с ответами для Всероссийской олимпиады по праву 
Мы поможем в написании ваших работ! ЗНАЕТЕ ЛИ ВЫ?
Влияние общества на человека
Приготовление дезинфицирующих растворов различной концентрации Практические работы по географии для 6 класса Организация работы процедурного кабинета Изменения в неживой природе осенью Уборка процедурного кабинета Сольфеджио. Все правила по сольфеджио Балочные системы. Определение реакций опор и моментов защемления |
Read the text and find the information about the purpose of creating the standard and who it was established for.Содержание книги
Похожие статьи вашей тематики
Поиск на нашем сайте
Л.К.Сальная
IT PROTECTION
Л.К.Сальная
IT Protection
Учебное пособие
для студентов второго образовательного уровня
Таганрог 2010
ББК 81.2Англ IT Protection: Учебное пособие / Сост. Л. К. Сальная – 174 с. Под общей редакцией Г. А. Краснощековой
Учебное пособие IT Protection предназначено для студентов второго образовательного уровня, может быть интересным в качестве дополнительного материала для чтения для магистрантов и аспирантов специальностей в области информационной безопасности.
В качестве учебного материала в пособии используются англоязычные тексты, взятые из оригинальных печатных и электронных источников, посвященные различным направлениям защиты информации. Учебное пособие предназначено для использования в учебном процессе при обучении студентов третьего и четвертого курсов специальностей в области информационной безопасности. Материал учебного пособия направлен на формирование профессионально-ориентированной коммуникативной компетенции студентов по направлению их будущей деятельности в области информационной безопасности. Структура учебного пособия сформирована в соответствии с поставленной задачей. Пособие содержит деcять основных разделов (unit), каждый из которых включает следующие подразделы: задания для тренировки произношения терминов (), работа с лексикой раздела (vocabulary), работа с аутентичными текстами (texts), задания для работы по переводу со словарем (vocabulary tasks), работа по освоению той части английской грамматики, которая характерна для научно-технической литературы (grammar), а также разделы writing и communication, позволяющие студентам формировать навыки письменного и устного профессионально-ориентированного иноязычного общения в наиболее типичных ситуациях. Учебное пособие предназначено для аудиторной и внеаудиторной (групповой и индивидуальной) работы. Каждый из основных разделов пособия (unit), содержит учебный текст для аудиторной работы с предтекстовыми заданиями, вопросами и лексическими заданиями разного уровня сложности и дополнительный текст для самостоятельной работы. Работа с грамматикой в пособии начинается с установления уровня сформированности лингвистической компетенции при помощи тестов остаточных знаний трех уровней сложности в подразделе грамматики первого раздела (Unit 1). Грамматический минимум пособия охватывает основной грамматический материал, касающийся особенностей научно-технической литературы, и содержит упражнения различного уровня сложности (A, B, C). В целом, задания направлены на формирование профессионально-ориентированной коммуникативной компетенции студентов в сфере будущей профессиональной деятельности и готовят студентов к профессионально-ориентированному иноязычному общению: поиску работы, интервью, общению с коллегами, партнерами, деловым поездкам. Все англоязычные тексты, используемые в пособии, взяты из оригинальной литературы: стандартов, научных статей, руководств пользователя информационными системами. Они сокращены, но не адаптированы. Разноуровневые упражнения к текстам направлены на формирование умений ознакомительного и изучающего чтения, а также профессионально-ориентированной коммуникативной компетенции. Основные темы текстов, которые представлены в пособии, это – методы и средства обеспечения безопасности информационных технологий, критерии оценки безопасности, в части функциональных требований и требований доверия, анализ рисков и управление безопасностью, криптографические методы и методы криптоанализа, способы и методы защиты информации в глобальных сетях и интрасетях. В конце пособия представлен поурочный словарь.
UNIT 1. COMMON CRITERIA SECURITY EVALUATION Memorize the terms 1. Read the following terms and their definitions and memorize them: availability – the protection of IT products so that they can be used by the intended user only software – programs that give instructions to the computer hardware and control its work unauthorized disclosure – an access to IT products or systems performed by a person who doesn’t have rights to do it threat – an act that can cause the breakdown of information protection system, e.g. threat of unauthorized disclosure tolerable – acceptable, receivable, e.g. tolerable risk procurement – purchase malicious – evil-minded, having some evil purpose, e.g. a malicious act implement – carry into effect, bring into action, perform confidentiality – a category of information protection that involves measures to keep the information secret and secure it from unauthorized disclosure 2. Match the following words with their Russian equivalents:
3. Match the following words with their synonyms:
Reading Pre-reading task. What sort of information should be protected? What measures can be taken to protect information? What do you know about Common Criteria Security Evaluation? Comment on the phrase “People who have information rule the world”. Answer the questions What is the reason for creating this standard? What is the sphere of application of CC? What is meant by TOE? Which parties use the standard? How? What are the main types of failure of security? What are the categories of protection related to them? Vocabulary tasks Make the word combinations.
Test B. Present Perfect. 1. All people in Australia (share) its national passion – surfing. 2. We (go) to my sister’s wedding next month. 3. What you (be) busy with? – I just (write) the report and now I (read) my e-mail. 4. What she (do)? – She (be) an artist. She just (finish) the college and (think) of changing the place of work now. 5. You still (cook)? – No, I already (cook) dinner. 6. I (envy) you. You (cook) so quickly. 7. Where you (go)? – We (go) for a run. 8. When I (go) home, I (take) you. Test C. Communication. Discuss your plans for the course. Distinguish the sphere of your scientific and professional interests, present and discuss it with your group-mates.
Unit 2. COST/BENEFIT ANALYSIS OF THE RISK Memorize the terms 1. Read the following terms and their definitions and memorize them: estimate risk – assess the risk of breaking the security system unacceptable risk – risk that can result in too high loss or damage of the information system or/of the enterprise under protection facility – building, construction, machine, device or work tool access point – entry point into a computer or a program of the computer, entrance places of a facility (doors, windows etc.) undesired event – act or incident that can have negative results respective critical asset – resources, capital, facilities or information that might be used illegally environmental impact statement – document that contains the results of the analysis of ecological effect 2. Match the following words with their Russian equivalents:
3. Match the following words with their synonyms:
Reading Pre-reading task. What measures can be used to persuade the managers to use security system? What should be done to keep the high level of an enterprise security? Characterize Facility 2. Identify Undesirable Events & Critical Assets Determine Consequences Define Threats Upgrade the System Estimate Risks Answer the questions What are the first steps of the cost/benefit risk analysis? Where can the information for the description of the facility be found? What is a generic fault tree made for? What should be done if the risk is estimated as unacceptable? What are the results of undesired events? Vocabulary tasks Make the word combinations
Complete the text. Events, weapons, to estimate, use, threat Threat Definition. Before a vulnerability analysis can be completed, a description of the 1) … is required. This description includes the type of adversary, tactics, and capabilities (number in the group, 2) …, equipment, and transportation mode). Also, information is needed about the threat 3) … the likelihood that they might attempt the undesired 4) …. The specific type of threat to a facility is referred to as the design basis threat (DBT). The DBT is often reduced to several paragraphs that describe the number of adversaries, their modus operandi, the type of tools and weapons they would 5) …, and the type of events or acts they are willing to commit. Translate into English. Специалист, несущий ответственность за выполнение заданий по оценке риска должен ясно представлять области, которые охватывает информационная безопасность. В первый год работы программы УИР руководитель должен уделить 50-75% своего времени установке и выполнению комплекса задач УИР (IRM). Термин «угроза» обозначает события, которые могут иметь неблагоприятные последствия. Управление информационными рисками – сложный процесс, требующий постоянного анализа рисков. Вопросы безопасности должны быть неотъемлемой частью разработки компьютерных приложений. Хорошо спланированная и выполненная оценка риска должна эффективно определять и измерять последствия широкого спектра угроз. Количественная и качественная метрические схемы, применяемые для измерения элементов риска, были впервые разработаны Национальным бюро стандартов.
Risk Estimation Risk is quantified by the following equation: R = PA * (1-PE) * C Where: R = risk associated with adversary attack PA = likelihood of the attack PE = likelihood that the security system is effective against the attack (1 – PE) = likelihood that the adversary attack is successful (also the likelihood that security system is not effective against the attack) C = consequence of the loss from the attack. Upgrades and Impacts If the estimated risk for the threat spectrum is judged to be unacceptable, upgrades to the system may be considered. The first step is to review all assumptions that were made that affect risk. All assumptions concerning undesired events, target identification, consequence definition, threat description, estimation of likelihood of attack, and safeguards functions should be carefully reevaluated. Upgrades to the system might include retrofits, additional safeguard features, or additional safety mitigation features. The upgraded system can then be analyzed to calculate any changes in risk due to change in likelihood of attack, system effectiveness, or consequence values. If the estimated risk for the upgraded system is judged to be acceptable, the upgrade is completed. If the risk is still unacceptable, the upgrade process of assumption review and system improvement should be repeated until the risk is judged to be acceptable. Once the system upgrade has been determined, it is important to evaluate the impacts of the system upgrade on the mission of the facility and the cost. If system upgrades put a heavy burden on normal operation, a trade-off would have to be considered between risk and operations. Budget can be the driver in implementing security upgrades. A trade-off between risk and total cost may have to be considered. When balance is achieved in the level of risk and upgrade impact on cost, mission, and schedule, the upgraded system is ready for implementation. At this point, the design/analysis process is complete. Grammar Active Voice.
Grammar tasks Communication Writing.
Unit 3. METHODS OF CRYPTOGRAPHY. Memorize the terms 1. Read the following terms and their definitions and memorize them: encryption – the process of coding a message using a cryptographic algorithm decryption – the reverse process plaintext – unencrypted message, text before sending and encryption eavesdropper – person that doesn’t have the authority to read the message, someone who tries to get the contents illegally authenticate information – verify the identity of information optional authentication of the client – additional identification and verification of the client man-in-the middle-attack – a type of attack when there is an eavesdropper between the sender and the receiver 2. Match the following words with their Russian equivalents:
3. Match the following words with their synonyms:
Reading Pre-reading task. Answer the questions What are the main terms of cryptography? What can be a plaintext? What should a specialist take into account when he wants to create his own or use some developed products? Vocabulary tasks Make the word combinations
Translate into English Хотя существует много алгоритмов и ключей, обладающих этим свойством, алгоритм РСА (названный в честь его разработчиков Р. Райвеста, А.Шамира и Л.Эйдмана) стал практически синонимом криптографических систем с открытым ключом. Рассмотрим сначала, как работает алгоритм РСА. Предположим, Боб хочет отправить зашифрованное сообщение. РСА состоит из двух взаимосвязанных компонентов: – выбора открытого и закрытого ключа, – алгоритмa зашифрования и расшифрования. Translate into English DES алгоритм является первым примером широкого производства и внедрения технических средств в область защиты информации. К настоящему времени выпускается несколько десятков устройств аппаратно - программной реализации DES-алгоритма. Для выпуска такого рода устройства необходимо получить сертификат Национального Бюро Стандартов на право реализации продукта, который выдается только после всесторонней проверки по специальным тестирующим процедурам. Достигнута высокая скорость шифрования. По некоторым сообщениям, в одном из устройств на основе специализированной микросхемы она составляет около 45 Мбит/сек. Основные области применения DES-алгоритма: - хранение данных в ЭВМ (шифрование файлов, паролей); - электронная система платежей (между клиентом и банком); - электронный обмен коммерческой информацией (между покупателем и продавцом). Grammar Passive Voice
Communication. Writing.
Unit 4. MODERN METHODS OF CRYPTANALYSIS. Memorize the terms 1. Read the following terms and their definitions and memorize them: incomprehensible ciphertext – encrypted message that is impossible to read and understand remove one bit of drudgery – simplify monotonous work overlapping superencipherment groups – partial matching of encrypted messages avalanche property of DES - changing a single bit in a DES key results in every bit of the enciphered block being changed randomly after only a few rounds ciphertext-only solution – process of decryption when cryptanalyst has only encrypted text to recover the plaintext mimic the process – imitate, simulate the process flaw – disadvantage, demerit, weak point in the system 2. Match the following words with their Russian equivalents:
3. Match the following words with their synonyms:
Reading Pre-reading task. What do you know about cryptanalysis? What cryptographic algorithms can you name? Text 1. Cryptanalysis. Cryptanalysis is hard work, requiring a willingness to endure many false starts, and a painstaking attention to detail. It requires intelligence to see subtle patterns in incomprehensible ciphertext. Automated aids to cryptanalysis come in many forms. Some collected statistical information about ciphertexts, thus removing one bit of drudgery from human shoulders. Others, such as the Bombe used in attacking the German Enigma, or the DES cracker built by the Electronic Frontier Foundation, or the converted unit record equipment (punched card machines) which compared Japanese code messages to one another at various displacements to find messages with overlapping superencipherment groups, work by trying thousands, or millions, of possibilities, one after another. Neither of these techniques is adequate to deal with many cipher systems, particularly modern ones. A well-designed cipher will not offer a simple opportunity to try different possibilities to find partial information about the key, and will have a key large enough to make trying every possible key hopeless. Nor is ordinary statistical information about the frequencies and contacts of bytes in the ciphertext likely to be much use. Thus, approaches taken from the field of AI (artificial intelligence) have been tried. In these approaches, it is attempted to combine the speed of the computer with steps that at least slightly move towards the skill and judgement of a human cryptanalyst. Hill-climbing Because the individual bits of the subkeys in DES are actual bits taken from the 56-bit DES key, an approach like the following to recover a DES key must have occurred to many people. Given a block of known plaintext, and its corresponding ciphertext, starting with a random 56-bit possible key, do the following: · Encipher the known plaintext with that key, and with every one of the 56 other keys obtained by inverting one bit of that key. · Compare the resulting ciphertext to the actual ciphertext. · In those of the 56 cases where the flipped bit results in the ciphertext produced differing in fewer bits from the actual ciphertext than that produced by the original trial key, invert that bit of the trial key to obtain the next trial key. This is a simple example of a hill-climbing algorithm, where the number of bits by which a trial encipherment differs from the actual ciphertext is a measure of one's (lack of) altitude. It would, however, never work against DES. That is because of the avalanche property of DES; changing a single bit in a DES key results in every bit of the block being enciphered being changed randomly after only a few rounds. Thus, even attempting to improve the hill climbing algorithm above by, for each trial, enciphering the known plaintext for eight rounds with the trial key, and deciphering the actual ciphertext for eight rounds with the trial key, and then determining the number of bits by which these two results differed would not be enough to help. Another idea would be to choose two rounds of DES, and by determining the input to those rounds by enciphering the known plaintext by the previous rounds, and the required output from those rounds by deciphering the actual ciphertext by the following rounds, examine the two 48-bit subkeys for the rounds, and, by examining the four possibilities for each group of 6 bits in those subkeys to produce the required change in each half of the block, find those which are consistent with the origin of those two subkeys from the original 56-bit key, and then try the resulting new 56-bit key or keys on the basis that it or they might be improvements over the preceding trial key. Genetic Programming A thesis by A. J. Bagnall described the ciphertext-only solution of some simple rotor machines by means of the technique of genetic programming. Genetic programming is a method by which a computer produces an answer to a question, or even a computer program to perform a task, by mimicing the process of natural selection. As noted in the thesis, and in the book Artificial Life by Stephen Levy, this technique was originated by John Holland in the mid-1960s, and his student David Goldberg was one of the first to refine the technique so that it could be used in practice with real problems of importance. It can be thought of as a special case of the hill-climbing algorithm, in that a quantitative measure of how "warm" the computer is in approaching the desired solution is required. Programs or answers must be in the form of a chain of discrete elements, such that there is at least a reasonable likelihood that a chain formed by taking one chain, and replacing a span of elements within it by the corresponding elements from another chain, will "make sense". Random mutations are also usually used, although genetic crossover has been found to be much more important. Starting with a random selection of solutions, those that work best are retained, and used as the parents of the next generation of solutions to be tried. Often, this retention is also randomized, so that better solutions have a higher probability of being retained. One type of mutation that happens in real life has not, to my knowledge, been used for genetic programming yet. Occasionally, plants and animals will increase the size of their genetic inheritance by duplicating part of it. Thus, a finite state machine could mutate by becoming a machine with twice as many states. It might be useful to make provision for this where a problem might be more complex to solve than initially realized. Answer the questions What automated aids to cryptanalysis do you remember? Characterize them in a few words. What are the approaches to cryptanalysis? What are the specific feature and potential of AI approach? What fact is the idea of hill-climbing algorithm based on? What does avalanche property of DES mean? What are the tendencies in genetic programming? Vocabulary tasks Make the word combinations
Complete the text. Given a block of known plaintext, and its corresponding …, starting with a random 56-bit possible key, do the following: · … the known plaintext with that key, and with every one of the 56 other keys obtained by inverting one bit of that key. · Compare the resulting ciphertext to the … ciphertext. · In those of the 56 cases where the flipped bit results in the ciphertext produced … in fewer bits from the actual ciphertext than that produced by the original trial key, invert that bit of the trial key to obtain the next trial key. This is a simple example of a … algorithm, where the number of bits by which a trial encipherment differs from the actual ciphertext is a measure of one's (lack of) altitude. Differential Cryptanalysis However, if one is fortunate enough to have a large quantity of corresponding plaintext and ciphertext blocks for a particular unknown key, a technique called differential cryptanalysis, developed by Eli Biham and Adi Shamir, is available to obtain clues about some bits of the key, thereby shortening an exhaustive search. After two rounds of DES, knowing both the input and output, it is trivial to determine the two subkeys used, since the outputs of both f-functions are known. For each S-box, there are four possible inputs to produce the known output. Since each subkey is 48 bits long, but the key is only 56 bits long, finding which of the four possibilities is true for each group of six bits in the subkeys is a bit like solving a crossword puzzle. Once the number of rounds increases to four, the problem becomes much harder. However, it is still true that the output depends on the input and the key. For a limited number of rounds, it is inevitable, without the need for any flaws in the S-boxes, that there will be some cases where a bit or a combination of bits in the output will have some correlation with a simple combination of some input bits and some key bits. Ideally, that correlation should be absolute with respect to the key bits, since there is only one key to solve for, but it can be probabilistic with respect to the input and output bits, since there need to be many pairs to test. As the number of rounds increases, though, the simple correlations disappear. Differential cryptanalysis represents an approach to finding more subtle correlations. Instead of saying "if this bit is 1 in the input, then that bit will be 0 (or 1) in the output", we say "changing this bit in the input changes (or does not change) that bit in the output". In fact, however, a complete pattern of which bits change and do not change in the input and in the output is the subject of differential cryptanalysis. The basic principle of differential cryptanalysis, in its classic form, is this: the cipher being attacked has a characteristic if there exists a constant X such that given many pairs of plaintexts A, B, such that B = A xor X, if a certain statement is true about the key, E(B,k) = E(A,k) xor Y for some constant Y will be true with a probability somewhat above that given by random chance. Linear Cryptanalysis Linear cryptanalysis, invented by Mitsuru Matsui, is a different, but related technique. Instead of looking for isolated points at which a block cipher behaves like something simpler, it involves trying to create a simpler approximation to the block cipher as a whole. For a great many plaintext-ciphertext pairs, the key that would produce that pair from the simplified cipher is found, and key bits which tend to be favored are likely to have the value of the corresponding bit of the key for the real cipher. The principle is a bit like the summation of many one-dimensional scans to produce a two-dimensional slice through an object in computer-assisted tomography. Truncated differentials It is of course possible that some of the bits of E(A,k) xor E(B,k) will be more likely to match those of Y than others. If one can, in addition, ignore some of the bits of A and B, one has a truncated differential for the cipher being attacked, and this technique, due to Lars R. Knudsen, has been found to be very powerful. (Being able to ignore some bits of A and B may allow two or more truncated differentials to be used together, and this is why it is important.) Higher-order Differentials Another important addition to the available techniques deriving from differential cryptanalysis is the use of higher-order differentials, which first appeared in a paper by Xuejia Lai. A differential characteristic of the type described above, where for a large number of different values of A, B equals A xor X, and the encrypted versions of A and B for a given key, k, are expected to have the relation E(A,k) = E(B,k) xor Y, if a target statement about the key k is true, can be made analogous to a derivative in calculus, and then it is termed that Y is the first derivative of the cipher E at the point X. A second-order derivative would then be one involving a second quantity, W, such that E(A,k) xor E(B,k) = E(C,k) xor E(D,k) xor Z is expected to be true more often than would be true due to chance, where not only is B = A xor X, but C = A xor W and D = B xor W. In that case, Z is the second derivative of the cipher E at the point X,W. Since xor performs the function of addition and subtraction, the four items encrypted for any A are just lumped together in this case, but if differential cryptanalysis were being performed over another field where the distinction is significant, then Y=E(A+X,k)-E(A,k) and Z=(E(A+X+W,k)-E(A+W,k))-(E(A+X,k)-E(A,k)) would be the appropriate equations to use. This technique is important because a second order derivative can exist at a point for the first coordinate of which no first order derivative exists, or is probable enough to be useful. And similarly, a third order derivative is derived from the difference of two second order derivatives, based on another constant difference, and so on. The Boomerang Attack Recently, a means of improving the flexibility of differential cryptanalysis was discovered by David A. Wagner. Called the boomerang attack, it allows the use of two unrelated characteristics for attacking two halves of a block cipher. This diagram shows how the attack might work if everything goes perfectly for a particular initial block. The numbered points in the diagram show the steps involved in the attack. 1. Start with a random block of plaintext. Based on the characteristic known for the first half of the cipher, if we XOR a certain vector with it, called d1 (equal to 00100000 in the diagram), the result after half-enciphering the two plaintext blocks, before and after the XOR, will differ by c1 (equal to 00110110 in the diagram), if what we wish to learn about the key happens to be true.
2. Since the characteristic applies only to the first half of the cipher, the results after the whole block cipher won't be related. Take those two results, and XOR each one with d2 (equal to 01001011 in the diagram), which is the vector corresponding to the characteristic for the second half of the cipher. In each case, XORing d2 with a ciphertext block is expected to change the result after deciphering halfway by c2 (equal to 00010000 in the diagram), again, if something is true of the key. 3. With two intermediate results that differ by c1, if each one has c2 XORed to it, the two results of the XOR will still differ by c1. Since this difference now relates to the first half characteristic, it can be seen in the final output, thus indicating the truth or otherwise of two hypotheses about the key. This increases the potential effectiveness of differential cryptanalysis, because one can make use of characteristics that do not propagate through the complete cipher. Also, certain kinds of added complexities, such as a bit transpose in the middle of the cipher, do not serve as a barrier to this method, since two values differing by an XOR with some value merely differ by an XOR with some other value after a bit transpose. However, it has its limitations. It only produces a result if both characteristics are present; it does not allow testing for each characteristic independently. Even so, it seems to double the number of rounds a cipher needs to be considered secure. Since at one end of a sequence of rounds, the precise difference between blocks that is required for the characteristic must be input, it isn't possible directly to cascade this method to break a block cipher into four or more pieces. Note that any single Feistel round has a large family of "characteristics" that is 100% probable, but which tells nothing about the key, since any pattern that involves leaving the half that is input to the F-function unchanged, but involves an XOR to the half that is XORed with the output of the F-function applies, so one of the things this method can do is allow the use of attacks against the first or last 15 rounds of DES against 16-round DES. Hence, if by some other trick a block cipher with 16 rounds could be broken into 16 pieces like this, one could test for an informative characteristic which applied to any single round. Grammar Active and Passive Voice. Grammar tasks. Communication. Writing.
Unit 5. STEGANOGRAPHY. Memorize the terms 1. Read the following terms and their definitions and memorize them: coin a term – invent and introduce carrier text - – place where secret message is kept steganography medium – concept that includeshidden_message, carrier and steganography_key semagram – secret message where any symbols can be used except letters and figures doodle – flourish, dash grille cipher – cipher that can be decrypted using special grid put on the message hidden in the carrier text retrieve the hidden text – restore, reconstruct the secret message 2. Match the following words with their Russian equivalents:
3. Match the following words with their synonyms:
Reading Pre-reading task. Look at the title of the text. What information do you expect to read here? What would you like to know about steganography? Where have you met steganographic techniques? Answer the questions What is the purpose of steganography? How is steganography related to cryptography? What was the early use of cryptography? What is carrier? Steganography medium? What is the application of steganography nowadays? Vocabulary tasks Make the word combinations
Null Ciphers Historically, null ciphers are a way to hide a message in another without the use of a complicated algorithm. One of the simplest null ciphers is shown in the classic examples below: PRESIDENT'S EMBARGO RULING SHOULD HAVE IMMEDIATE NOTICE. GRAVE SITUATION AFFECTING INTERNATIONAL LAW. STATEMENT FORESHADOWS RUIN OF MANY NEUTRALS. YELLOW JOURNALS UNIFYING NATIONAL EXCITEMENT IMMENSELY. Digital Image and Audio Many common digital steganography techniques employ graphical images or audio files as the carrier medium. It is instructive, then, to review image and audio encoding before discussing how steganography and steganalysis works with these carriers. Figure 2 shows the RGB color cube, a common means with which to represent a given color by the relative intensity of its three component colors—red, green, and blue—each with their own axis (moreCrayons 2003). The absence of all colors yields black, shown as the intersection of the zero point of the three-color axes. The mixture of 100 percent red, 100 percent blue, and the absence of green form magenta; cyan is 100 percent green and 100 percent blue without any red; and 100 percent green and 100 percent red with no blue combine to form yellow. White is the presence of all three colors.
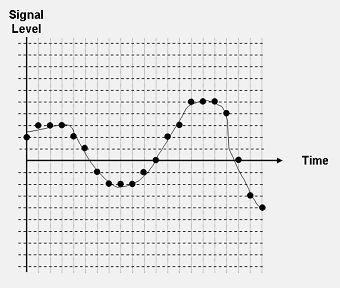
Most digital image applications today support 24-bit true color, where each picture element (pixel) is encoded in 24 bits, comprising the three RGB bytes as described above. Other applications encode color using eight bits/pix. These schemes also use 24-bit true color but employ a palette that specifies which colors are used in the image. Each pix is encoded in eight bits, where the value points to a 24-bit color entry in the palette. This method limits the unique number of colors in a given image to 256 (2^8). The choice color encoding obviously affects image size. A 640 X 480 pixel image using eight-bit color would occupy approximately 307 KB (640 X 480 = 307,200 bytes), whereas a 1400 X 1050 pix image using 24-bit true color would require 4.4 MB (1400 X 1050 X 3 = 4,410,000 bytes). Color palettes and eight-bit color are commonly used with Graphics Interchange Format (GIF) and Bitmap (BMP) image formats. GIF and BMP are generally considered to offer lossless compression because the image recovered after encoding and compression is bit-for-bit identical to the original image (Johnson and Jajodia 1998A). The Joint Photographic Experts Group (JPEG) image format uses discrete cosine transforms rather than a pix-by-pix encoding. In JPEG, the image is divided into 8 X 8 blocks for each separate color component. The goal is to find blocks where the amount of change in the pixel values (the energy) is low. If the energy level is too high, the block is subdivided into 8 X 8 subblocks until the energy level is low enough. Each 8 X 8 block (or subblock) is transformed into 64 discrete cosine transforms coefficients that approximate the luminance (brightness, darkness, and contrast) and chrominance (color) of that portion of the image. JPEG is generally considered to be lossy compression because the image recovered from the compressed JPEG file is a close approximation of, but not identical to, the original (Johnson and Jajodia 1998A; Monash University 2004; Provos and Honeyman 2003). Audio encoding involves converting an analog signal to a bit stream. Analog sound—voice and music—is represented by sine waves of different frequencies. The human ear can hear frequencies nominally in the range of 20-20,000 cycles/second (Hertz or Hz). Sound is analog, meaning that it is a continuous signal. Storing the sound digitally requires that the continuous sound wave be converted to a set of samples that can be represented by a sequence of zeros and ones. Analog-to-digital conversion is accomplished by sampling the analog signal (with a microphone or other audio detector) and converting those samples to voltage levels. The voltage or signal level is then converted to a numeric value using a scheme called pulse code modulation. The device that performs this conversion is called a coder-decoder or codec. Pulse code modulation provides only an approximation of the original analog signal, as shown in Figure 4. If the analog sound level is measured at a 4.86 level, for example, it would be converted to a five in pulse code modulation. This is called quantization error. Different audio applications define a different number of pulse code modulation levels so that this "error" is nearly undetectable by the human ear. The telephone network converts each voice sample to an eight-bit value (0-255), whereas music applications generally use 16-bit values (0-65,535) (Fries and Fries 2000; Rey 1983).
Analog signals need to be sampled at a rate of twice the highest frequency component of the signal so that the original can be correctly reproduced from the samples alone. In the telephone network, the human voice is carried in a frequency band 0-4000 Hz (although only about 400-3400 Hz is actually used to carry voice); therefore, voice is sampled 8,000 times per second (an 8 kHz sampling rate). Music audio applications assume the full spectrum of the human ear and generally use a 44.1 kHz sampling rate (Fries and Fries 2000; Rey 1983). The bit rate of uncompressed music can be easily calculated from the sampling rate (44.1 kHz), pulse code modulation resolution (16 bits), and number of sound channels (two) to be 1,411,200 bits per second. This would suggest that a one-minute audio file (uncompressed) would occupy 10.6 MB (1,411,200*60/8 = 10,584,000). Audio files are, in fact, made smaller by using a variety of compression techniques. One obvious method is to reduce the number of channels to one or to reduce the sampling rate, in some cases as low as 11 kHz. Other codecs use proprietary compression schemes. All of these solutions reduce the quality of the sound. Grammar. Modal Verbs. Употребление. Выражение предложения. Would you like, shall I/ shall we – вежливое предложение. Would you like some coffee please? Хотите кофе? Shall we buy him a present? Купим ему подарок? Выражение просьбы. Сan – просьба. Can you help me finish my work? Поможешь мне закончить работу? Сould – вежливая просьба). Could I have some more paper? Можно мне еще лист бумаги? Will – неформальная просьба. Will you help me? Ты поможешь мне? Выражение совета. Выражение запрета. Mustn’t, сan’t – запрет. You mustn’t park here. Здесь нельзя парковаться. You can't enter this room. It's room for the staff. Эта комната для персонала. Вам туда нельзя. Grammar tasks Communication.
Writing. Write an abstract of the material you’d like to present at the conference (see Appendix 3).
Unit 6. QUANTUM CRYPTOGRAPHY Memorize the terms 1. Read the following terms and their definitions and memorize them: Eavesdrop – overhear, intercept random result – probabilistic, patternless choice insecure channel – unprotected channel that can be easily eavesdropped expand on an idea – study and speak in detail about an idea be a bit off – be switched over, changed a bit prearranged code – discussed beforehand secure – protected, safe discrepancy – difference, diversity be bugged – be overheard measure – scale, determine 2. Match the following words with their Russian equivalents: <
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Последнее изменение этой страницы: 2017-01-27; просмотров: 563; Нарушение авторского права страницы; Мы поможем в написании вашей работы! infopedia.su Все материалы представленные на сайте исключительно с целью ознакомления читателями и не преследуют коммерческих целей или нарушение авторских прав. Обратная связь - 18.119.119.119 (0.012 с.) |