Заглавная страница Избранные статьи Случайная статья Познавательные статьи Новые добавления Обратная связь FAQ Написать работу КАТЕГОРИИ: ТОП 10 на сайте Приготовление дезинфицирующих растворов различной концентрацииТехника нижней прямой подачи мяча. Франко-прусская война (причины и последствия) Организация работы процедурного кабинета Смысловое и механическое запоминание, их место и роль в усвоении знаний Коммуникативные барьеры и пути их преодоления Обработка изделий медицинского назначения многократного применения Образцы текста публицистического стиля Четыре типа изменения баланса Задачи с ответами для Всероссийской олимпиады по праву 
Мы поможем в написании ваших работ! ЗНАЕТЕ ЛИ ВЫ?
Влияние общества на человека
Приготовление дезинфицирующих растворов различной концентрации Практические работы по географии для 6 класса Организация работы процедурного кабинета Изменения в неживой природе осенью Уборка процедурного кабинета Сольфеджио. Все правила по сольфеджио Балочные системы. Определение реакций опор и моментов защемления |
Virtualization Resource RequirementsСодержание книги
Поиск на нашем сайте
Microsoft, VMware, and other vendors produce virtualization environments. This list of require-ments is based on the requirements for Microsoft’s Windows Virtual PC product.
A PC suitable for virtualization should have the following minimum hardware requirements:
1GHz or faster processor 32-bit or 64-bit 2GB or more RAM
15GB hard disk space for each Windows VM Windows 7 Home Premium or higher
In addition to these base requirements, the following hardware features will help improve the per-formance of the host and guest operating systems:
Hardware-assisted virtualization features in the processor (must also be enabled in the sys-tem BIOS)
2GB of RAM or more per each VM 132 CompTIA A+ Quick Reference
Emulator Requirements and Features
Microsoft offers two different virtualization environments for client PCs: Virtual PC 2007 and Windows Virtual PC. Their differences are summarized in Table 6-16.
Table 6-16 Virtual PC 2007 and Windows Virtual PC Requirements and Features
Security Requirements
Virtualized environments need to be secured at both physical hardware and VM levels. Industry recommendations include the following:
Practice the same security features for VMs as for desktops (antivirus, physical security, firewalls, security patches for the operating system and applications)
Maintain administrator-only access to the VM host software Disable unneeded services and virtual hardware in the VM Chapter 6: Operating Systems 133
Figure 6-14 A Windows XP mode VM running in Windows Virtual PC.
Network Requirements
To enable a VM to connect to network resources (NIC, Internet, and so on) available on the host machine, the VM needs to be connected to those resources. With Microsoft virtualization pro-grams, you need to install integration components supplied as part of the virtualization program. Once these components are integrated, you can use the host PC’s network connections to connect to the network and access the Internet.
Understanding Hypervisors
Desktop virtualization programs such as Virtual PC 2007 and Windows Virtual PC are examples of hosted virtualization. These programs are connected to the host operating system via a virtual machine monitor program (VMM) and all connections to hardware are virtualized.
A bare-metal virtualization program such as Microsoft Hyper-Z does not pass through a host operating system. Instead, its VMM, or hypervisor, connects directly to shared hardware, and VM connections to hardware can be passed via the hypervisor or directly between the VM and the hardware. Hypervisor virtualization is commonly used on server hardware.
This page intentionally left blank
Security
The 220-802 2.0 Security domain covers physical and digital security, common security threats, security best practices, data destruction and disposal methods, and securing small office/home office (SOHO) wireless and wired networks. This section accounts for 22% of the CompTIA A+ 220-802 exam.
Common Prevention Methods
The best way to deal with security threats is to prevent them. Prevention has two aspects: physical and digital. The following sections review what you need to know about these methods for the 220-802 exam.
Physical Security
Physical security is a blanket term for preventing physical access to confidential information. These methods include securing of the premises where information is stored, securing of documents, and preventing unauthorized personnel from gaining access to that information.
Door Locks and Access Methods
To prevent physical access to confidential information in a building, the first line of defense is a locked door. To permit access, the following methods can be used:
Physical key —Low cost, but allows access to anyone who has the key. Records should be keptof who has what keys and locks should be changed periodically.
Key pad —More expensive, but easier to change if unauthorized personnel discover the code.Change codes periodically for security.
Key fobs and RFID badges —Easy to carry, but also easy to lose. These use short-range radiosignals. Can be disabled if lost.
Security portals —Revolving doors or “mantraps” can be used to prevent tailgating.
Identifying the User: Smart Cards and Biometrics
A more thorough method of access control involves the use of smart cards. Smart cards identify the owner, provide access to specified areas of a building and computers, and can be used to digitally sign, encrypt, and email files using RSA encryption. They can be incorporated into a USB thumb drive, a key fob, or a card that resembles a credit card in size.
A typical smart card generates an authentication code at short intervals (typically 60 seconds), and the code must be entered and validated before access is granted. Some installations also require the use 136 CompTIA A+ Quick Reference
of a personal identification number (PIN). Some smart card products can also be embedded into smartphones and USB thumb drives.
Biometrics uses a reader or a scanner to evaluate a potential user’s physical characteristics before allowing entry or use. Biometrics systems compare a fingerprint or thumbprint (common on many laptop and portable devices) or a retinal scan (used in high-security buildings such as banks or prisons) to the store information for authorized users.
Physical Data Protection
To prevent unauthorized access to physical documents, follow these precautions:
Keep documents locked up and out of sight when not in use Shred documents when no longer needed
To prevent unauthorized access to digital files, follow these precautions:
Keep passwords out of sight; no sticky notes, please Use privacy filters to block side views of screens
Digital Security
Documents stored on a computer can be accessed by unauthorized users at the keyboard or remotely if they are not secure. Use the security practices in this section to keep digital informa-tion safe.
Figure 7-1 shows a layered defensive strategy that is designed to protect the user and data. Notice that the first line of defense is network based, the second line is on the local PC (host), and the third line of defense is the user.
Hackers
Port
Scanners
Virus
Infected
Files
Credit Card
Numbers
Passwords
Sensitive
Data
Figure 7-1 Layered defense. Chapter 7: Security 137
Antivirus
The first step in antivirus (AV) is to detect a suspicious file or program. AV employs a scanning engine that uses one or both of the following techniques:
Heuristics analyze the behavior and activity of a file or program. If it is replicating, scan-ning other files, or connecting to other computers, it is flagged as a virus. Unfortunately, this hypervigilance tends to cause many false positives because many legit programs do exactly those behaviors. Search tools and programs that verify software keys often set off a heuristic scanning engine.
The other method of detecting viruses is by comparing files to the signatures (often called definitions) of known viruses. Much like fingerprint analysis, the AV software receives updates from a database maintained by the software manufacturer. The drawback of this method lies in its inability to quickly identify new and emerging threats. A proper AV uses a combination of both techniques.
Scan early and scan often. Scanning takes considerable system resources, so perform scheduled updates and scans during off-peak hours.
Both the signatures and the engine need to be as updated as possible. This is best done by setting it to commence automatically during down times, such as at night and on holidays.
After a file or program is found to be a match either by its activity (heuristics) or via update of known virus signatures, one of three things happens to the file. If it can be cleaned (removed from the host file), it will be; if not, the file is quarantined. In other words, nothing can be written to or read from that place on the hard disk drive (HDD).
As a technician, to prevent reinfection, you need to determine how the computer became infected. The most common ways of catching a virus is not using AV, using an obsolete AV, and not using up-to-date virus definitions and scan engines. The following is a list of common remediation:
Install AV software Update definitions
Update patches and service packs for OS and applications Use virus removal features of the AV
Identify the source of infection
Firewalls
A good security plan uses layered defenses, including hardware and software firewalls. Firewalls work in three ways:
Packet filtering —The most common and straightforward. Firewalls that use packet filteringeither block or allow packets by using basic criteria, source or destination IP address, ports, or protocols. The disadvantage of packet filtering is that it is not subtle. It is a reliable but 138 CompTIA A+ Quick Reference
inflexible gate guard. Sometimes, legitimate packets get filtered because they are different. Packet filtering can be implemented in hardware or software.
Proxy filters —Inbound and outbound traffic pass through the proxy filter, which imitatesdirect connections between the computer and the Internet, but blocks harmful traffic. A proxy filter is usually implanted in a gateway server or an Internet appliance.
Stateful packet inspection (stateful protocol filter) —Looks for unfamiliar packets andblocks them. After a rogue packet enters the target network, a hacker never hears from it again. Stateful packet inspection can be implemented in hardware or software.
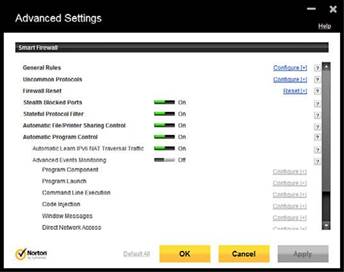
Figure 7-2 illustrates the stateful protocol filter and other advanced settings used by the Norton Internet Security Smart Firewall.
Figure 7-2 A firewall program with stateful protocol filter and other advanced settings (NortonInternet Security).
Hardware firewalls don’t impact the individual PC’s performance and can support an entire net-work.
Viruses, Worms, and Trojan Horses
Viruses are the oldest and best known form of malware. The name comes from their ability to spread from system to system through means such as email and infection of portable drives.
The most common type of virus today is a Trojan horse (Trojan). This type of program can mas-querade as an update to a video player, a free antivirus application, an unsolicited PDF attachment, or an ActiveX, Java, or JavaScript program hidden on a Facebook page under a short URL. When the Trojan activates, the payload goes to work erasing or encrypting files (sometimes with a ran- Chapter 7: Security 139
som message offering to unencrypt your file for a fee), turning your PC into a remotely controlled bot that can be used to attack other PCs, and so on.
Worms are self-replicating software that fill HDDs and modify and spread to others. Frequently, the terms worm and Trojan horse are often interchanged. However, in either case, antivirus pro-grams that are running in real time and have frequently (daily) updated definitions help protect the system.
Some search tools now provide warnings when you try to visit a page with a record of suspicious virus related activity.
Antispyware
Spyware programs relay information about your computer activities to a remote server. The information fetched by this type of malware can be used to display targeted advertisements or to transmit your Web browsing habits. The advertisements may be for fake products (such as fake antivirus or fake antispyware), so clicking the ads delivered by spyware can further compromise your computer.
Antispyware features can be built in to standalone security appliances that also act as firewalls and email filters or can be run on individual PCs. As with antivirus, the best protection comes from real-time always-on protection that is updated frequently.
Rootkits
A rootkit is malicious software designed to hide destructive activity on a system. Various types of malware make themselves very difficult to detect by hiding themselves with rootkits. Some clues of rootkit infection include changed system file names, file permissions that deny access to files, and files that are missing. Rootkits that hide themselves in the master boot record (MBR) are very difficult to find. Some antivirus programs also specifically target rootkits, but you can also use spe-cialized rootkit-removal programs, many of which are provided for free from major antivirus ven-dors. In some cases, it might be necessary to reinstall Windows to remove a rootkit in the MBR.
Phishing
Emails purporting to announce that you have won an email lottery, have a long-lost relative in another country who has left you a fortune, and fearsome-looking warnings to “Dear Customer” that your bank or PayPal account has been suspended are all examples of phishing.
Phishing is any attempt to get you to provide confidential information that can be exploited by another user for financial gain or even complete identity theft. Using email filtering and spam blocking helps reduce the number of phishing emails that arrive in a particular mailbox. Using a web browser Phishing filter helps to identify Phishing websites.
Shoulder Surfing
The annoying co-worker or outside technician who is right behind you as you log in to the corpo-rate network might actually be attempting to get your login information by “shoulder surfing.” If you think someone’s watching your login process, block the keyboard from their view or just do not log in until they move on. If it is an outside technician, check with your supervisor to make 140 CompTIA A+ Quick Reference
sure it’s a real technician and not an intruder trying to break in.
Change your password immediately if you think you have been shoulder surfed—before the intruder takes over your account. For systems that are in areas with a lot of foot traffic, it makes sense to install a privacy filter on the display to help block shoulder surfing from happening.
User Education
Customers are often the victims of computer attacks, ranging from random malware intent on causing untold damaged to selective premeditated identity theft. It is the technician’s responsibil-ity to educate the end user of potential threats and common preventive measures without causing unnecessary alarm. The following are common sources of viruses that users should be aware of the following:
Email attachments from known senders (because users are more likely to open attachments from a friend)
Free software downloads (especially free malware scans, desktop backgrounds, and screen savers)
Peer-to-peer file-sharing services offering music, movies, games and programs Copying and moving files among computers via a network or portable media
Helping users to stop these types of behavior and potential threats can go a long way towards mak-ing corporate networks and work-at-home PCs much more secure.
Positive steps to take include the following:
Scanning systems for malware of all types with updated antimalware software Scanning removable-media drives for malware
Reporting and removing detected infections Quarantining and reporting suspect files
Using antiphishing features in email and web browsers Disabling Windows AutoPlay with Group Policies
Least Privilege and User Account Control
The principle of least privilege is to grant users just enough privileges to use the computer and get their assigned work done, but not enough to compromise security.
Windows Vista and Windows 7 support this principle with User Account Control (UAC). When you set up users as Standard users, they have the rights needed to perform day-to-day tasks, but not to install programs or perform other activities that might harm the system.
When a Standard user needs to perform an activity beyond the scope of the privileges that have Chapter 7: Security 141
granted, a UAC prompt appears. The user needs to have the system’s administrator provide the password to continue the operation (see Figure 7-3).
Figure 7-3 A UAC prompt for a Standard user.
Keeping UAC enabled for Standard users is just one of the security best practices to follow. The following sections provide additional information.
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Последнее изменение этой страницы: 2017-02-08; просмотров: 261; Нарушение авторского права страницы; Мы поможем в написании вашей работы! infopedia.su Все материалы представленные на сайте исключительно с целью ознакомления читателями и не преследуют коммерческих целей или нарушение авторских прав. Обратная связь - 18.191.120.103 (0.009 с.) |





 Chapter 7
Chapter 7