Заглавная страница Избранные статьи Случайная статья Познавательные статьи Новые добавления Обратная связь КАТЕГОРИИ: ТОП 10 на сайте Приготовление дезинфицирующих растворов различной концентрацииТехника нижней прямой подачи мяча. Франко-прусская война (причины и последствия) Организация работы процедурного кабинета Смысловое и механическое запоминание, их место и роль в усвоении знаний Коммуникативные барьеры и пути их преодоления Обработка изделий медицинского назначения многократного применения Образцы текста публицистического стиля Четыре типа изменения баланса Задачи с ответами для Всероссийской олимпиады по праву 
Мы поможем в написании ваших работ! ЗНАЕТЕ ЛИ ВЫ?
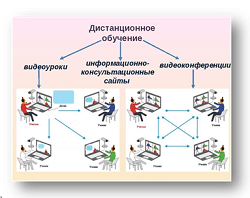
Влияние общества на человека
Приготовление дезинфицирующих растворов различной концентрации Практические работы по географии для 6 класса Организация работы процедурного кабинета Изменения в неживой природе осенью Уборка процедурного кабинета Сольфеджио. Все правила по сольфеджио Балочные системы. Определение реакций опор и моментов защемления |
Data Destruction and Disposal Methods
The old HDDs inside of old computers may still have valuable information—information that could be used to steal identities or trade secrets. The following sections review methods for mak-ing sure the information on a hard drive is rendered unretrievable.
Formatting and Drive Overwriting
When the Windows command Format is used on a hard disk with the Quick option, only the beginning of the disk where file records are stored is wiped out. The remainder of the disk’s con-tents are still intact until they are overwritten. Even if the Quick option is not used, it is an easy task for an unformat program to retrieve the data.
PATA and SATA drives do not support a true “low-level” format option, but setup programs pro-vided by vendors typically feature a zero overwrite option that fills the drive’s data areas with 0s. This prevents unformat programs from retrieving data, but more sophisticated data recovery pro-grams can still find much or all of the data.
Drive Wiping
If the drive needs to be kept in service but needs to be securely purged of all information, a drive wiping (also known as disk scrubbing or disk wiping) program that corresponds to U.S. Department of Defense 5220.22-M (7 passes) or Peter Gutmann’s 35-pass maximum security
method will prevent data recovery. Many commercial and freeware programs include either or both of these options. Figure 7-5 illustrates these and other disk wiping options in the popular open source program Eraser.
Figure 7-5 The open source Eraser disk wiping program offers DoD, Gutmann, and many otherdisk wiping options. Chapter 7: Security 145
Physical Disk Destruction
When keeping a hard disk in service is not a requirement, or if dealing with sensitive data on opti-cal or USB flash memory drives or floppy disks is a concern, physical disk destruction provides maximum security.
Hard disk platters can be destroyed with a drill, a hammer, or can be wiped with an electromag-netic degausser or a powerful permanent magnet. Degaussing is also effective on floppy disks, tape drives, and other types of magnetic media.
To destroy optical media, run it through a shredder designed for optical media.
To destroy USB flash drives, use a drill or a hammer to destroy the memory chips in the unit.
After destroying hard disks or USB drives, be sure to recycle the remains. Some electronic recy-clers will also destroy the drives for you, sometimes even as you watch.
Securing a SOHO Wireless Network
Although techniques such as Wi-Fi Protected Setup (WPS) and wizards built in to some versions of Windows are helping to make wireless networks more secure during installation, far too many wireless networks in small offices and home offices are wide open to intruders. Use the recom-mendations in Table 7-3 to help secure your wireless network.
|
||||
|
Последнее изменение этой страницы: 2017-02-08; просмотров: 296; Нарушение авторского права страницы; Мы поможем в написании вашей работы! infopedia.su Все материалы представленные на сайте исключительно с целью ознакомления читателями и не преследуют коммерческих целей или нарушение авторских прав. Обратная связь - 3.145.12.242 (0.005 с.) |