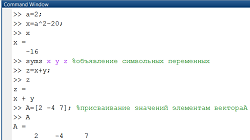
Заглавная страница Избранные статьи Случайная статья Познавательные статьи Новые добавления Обратная связь FAQ Написать работу КАТЕГОРИИ: ТОП 10 на сайте Приготовление дезинфицирующих растворов различной концентрацииТехника нижней прямой подачи мяча. Франко-прусская война (причины и последствия) Организация работы процедурного кабинета Смысловое и механическое запоминание, их место и роль в усвоении знаний Коммуникативные барьеры и пути их преодоления Обработка изделий медицинского назначения многократного применения Образцы текста публицистического стиля Четыре типа изменения баланса Задачи с ответами для Всероссийской олимпиады по праву 
Мы поможем в написании ваших работ! ЗНАЕТЕ ЛИ ВЫ?
Влияние общества на человека
Приготовление дезинфицирующих растворов различной концентрации Практические работы по географии для 6 класса Организация работы процедурного кабинета Изменения в неживой природе осенью Уборка процедурного кабинета Сольфеджио. Все правила по сольфеджио Балочные системы. Определение реакций опор и моментов защемления |
Text 8. Computer programming languageСодержание книги
Похожие статьи вашей тематики
Поиск на нашем сайте
Computer programming is any of various languages for expressing a set of detailed instructions for a digital computer. Such a language consists of characters and rules for combining them into symbols and words. Many kinds of programming languages have been developed over the years. Initially programmers had to write instructions in machine language. This coded language, which can be understood and executed directly by the computer without conversion or translation, consists of binary digits representing operation codes and memory addresses. Because it is made up of strings of Is and Os, machine language is difficult for humans to use. Assembly language was eventually devised for greater convenience. It enabled programmers to express instructions in alphabetic symbols (e.g., AD for add and SUB for subtract) rather than in numbers. Although assembly language with its mnemonic code was easier to use than machine language, it was clearly desirable to develop programming languages that more closely resembled human communication. The first so-called high-level language was FORTRAN (acronym for Formula Translation), invented in 1956. FORTRAN was well suited to scientists and mathematicians because it was similar to mathematical notations. It did, however, present some difficulty for those in nonmathematically oriented fields. As a result, a more practical programming language known as COBOL (Common Business-Oriented Language) was devised several years later (1960). COBOL employs words and syntax resembling those of ordinary English. Later, other languages even easier to learn and use were introduced. BASIC (Beginner's All-Purpose Symbolic Instruction Code), for example, can be readily mastered by the layperson and is used extensively in schools, businesses, and homes for microcomputer programming. С is a high-level language that can function as an assembly language; much commercial software is written in this flexible language. Another versatile language widely used for microcomputer as well as minicomputer applications is Pascal (probably named for the French scientist-philosopher Blaise Pascal). Other high-level programming languages possess unique features that make each one suitable for a specific application. Some examples are APT (Automatically Programmed Tools), for numerical control of industrial machine tools, and GPSS (General-Purpose Simulation System), for constructing simulation models. LISP (List Processing) can be used to manipulate symbols and lists rather than numeric data; it is often used in artificial-intelligence applications. Fourth-generation languages (4GLs) are closer to human language than are high-level (or third-generation) languages. They are used primarily for database management or as query languages; examples include FOCUS, SQL (Structured Query Language), and dBASE. Object-oriented programming languages, such as C++ and Smalltalk, write programs incorporating self-contained collections of data structure or computational instructions (called "objects"). New programs can be written by reassembling and manipulating the objects. Text 9. Computer-aided engineering (CAE) CAE in industry is the integration of design and manufacturing into a system under the direct control of digital computers. CAE combines the use of computers in industrial-design work, computer-aided design (CAD), with their use in manufacturing operations, computer-aided manufacturing (CAM). This integrated process is commonly called CAD/CAM. CAD systems generally consist of a computer with one or more terminals featuring video monitors and interactive graphics-input devices; they can be used to design such things as machine parts, patterns for clothing, or integrated circuits. CAM Systems involve the use of numerically controlled machine tools and high-performance, programmable industrial robots. In a CAE system, drawings developed and revised during the design process are converted directly into instructions for the production machines that will manufacture the desired object. CAE systems reduce the time needed to develop new products and increase productivity by optimizing production flow and scheduling and by providing greater flexibility in altering machine operations. Text 10. Computer simulation Computer simulation is the use of a computer to represent the dynamic responses of one system by the behaviour of another system modeled after it. A simulation uses a mathematical description, or model, of a real system in the form of a computer program. This model is composed of equations that duplicate the functional relationships within the real system. When the program is run, the resulting mathematical dynamics form an analog of the behaviour of the real system, with the results presented in the form of data. A simulation can also take the form of a computer-graphics image that represents dynamic processes in an animated sequence. Computer simulations are used to study the dynamic behaviour of objects or systems in response to conditions that cannot be easily or safely applied in real life. For example, a nuclear blast can be described by a mathematical model that incorporates such variables as heat, velocity, and radioactive emissions. Additional mathematical equations can then be used to adjust the model to changes in certain variables, such as the amount of fissionable material that produced the blast. Simulations are especially useful in enabling observers to measure and predict how the functioning of an entire system may be affected by altering individual components within that system. The simpler simulations performed by personal computers consist mainly of business models and geometric models. The former includes spreadsheet, financial and statistical software programs that are used in business analysis and planning. Geometric models are used for numerous applications that require simple mathematical modeling of objects, such as buildings, industrial parts, and the molecular structures of chemicals. More advanced simulations, such as those that emulate weather patterns or the behaviour of macroeconomic systems, are usually performed on powerful workstations or on mainframe computers. In engineering, computer models of newly designed structures undergo simulated tests to determine their responses to stress and other physical variables. Simulations of river systems can be manipulated to determine the potential effects of dams and irrigation networks before any actual construction has taken place. Other examples of computer simulations include estimating the competitive responses of companies in a particular market and reproducing the movement and flight of space vehicles. Text 11. Computer graphics Computer graphics is the use of computers to produce pictorial images. The images produced can be printed documents or animated motion pictures, but the term computer graphics refers particularly to images displayed on a video display screen, or display monitor. These screens can display graphic as well as alphanumeric data. A computer-graphics system basically consists of a computer to store and manipulate images, a display screen, various input and output devices, and a graphics software package — i.e., a program that enables a computer to process graphic images by means of mathematical language. These programs enable the computer to draw, colour, shade, and manipulate the images held in its memory. A computer displays images on the phosphor-coated surface of a graphics display screen by means of an electron beam that sweeps the screen many times each second. Those portions of the screen energized by the beam emit light, and changes in the intensity of the beam determine their brightness and hue. The brightness of the resulting image fades quickly, however, and must be continuously "refreshed" by the beam, typically 30 times per second. Graphics software programs enable a user to draw, colour, shade, and manipulate an image on a display screen with commands input by a keyboard. A picture can be drawn or redrawn onto the screen with the use of a mouse, a pressure-sensitive tablet, or a light pen. Preexisting images on paper can be scanned into the computer through the use of scanners, digitizers, pattern-recognition devices, or digital cameras. Frames of images on videotape also can be entered into a computer. Various output devices have been developed as well; special programs send digital data from the computer's memory to an imagesetter or film recorder, which prints the image on paper or on photographic film. The computer can also generate hard copy by means of plotters and laser or dot-matrix printers. Pictures are stored and processed in a computer's memory by either of two methods: raster graphics and vector graphics. Raster-type graphics maintain an image as a matrix of independently controlled dots, while vector graphics maintain it as a collection of points, lines, and arcs. Raster graphics are now the dominant computer graphics technology. In raster graphics, the computer's memory stores an image as a matrix, or grid, of individual dots, or pixels (picture elements). Each pixel is encoded in the computer's memory as one or several bits — i.e., binary digits represented by 0 or 1. A 2-bit pixel can represent either black or white, while a 4-bit pixel can represent any of 16 different colours or shades of gray. The constituent bits that encode a picture in the computer's memory are called a bit map. Computers need large processing and memory capacities to translate the enormous amounts of information contained in a picture into the digital code of a bit map, and graphics software programs use special algorithms (computional processes) to perform these procedures. In raster graphics, the thousands of tiny pixels that make up an individual image are projected onto a display screen as illuminated dots that from a distance appear as a contiguous image. The picture frame consists of hundreds of tiny horizontal rows, each of which contains hundreds of pixels. An electron beam creates the grid of pixels by tracing each horizontal line from left to right, one pixel at a time, from the top line to the bottom line. Raster graphics create uniform coloured areas and distinct patterns and allow precise manipulation because their constituent images can be altered one dot at a time. Their main disadvantage is that the images are subtly staircased — i.e., diagonal lines and edges appear jagged and less distinct when viewed from a very short distance. A corollary of television technology, raster graphics emerged in the early 1970s and had largely displaced vector systems by the '90s. In vector graphics, images are made up of a series of lines, each of which is stored in the computer's memory as a vector — i.e., as two points on an x-y matrix. On a vector-type display screen, an electron beam sweeps back and forth between the points designated by the computer and the paths so energized emit light, thereby creating lines; solid shapes are created by grouping lines closely enough to form a contiguous image. Vector-graphics technology was developed in the mid-1960s and widely used until it was supplanted by raster graphics. Its application is now largely restricted to highly linear work in computer-aided design and architectural drafting, and even this is performed on raster-type screens with the vectors converted into dots. Computer graphics have found widespread use in printing, product design and manufacturing, scientific research, and entertainment since the 1960s. In the business office, computers routinely create graphs and tables to illustrate text information. Computer-aided design systems have replaced drafting boards in the design of a vast array of products ranging from buildings to automotive bodies and aircraft hulls to electrical and electronic devices. Computers are also often used to test various mechanical, electrical, or thermal properties of the component under design. Scientists use computers to simulate the behaviour of complicated natural systems in animated motion-picture sequences. These pictorial visualizations can afford a clearer understanding of the multiple forces or variables at work in such phenomena as nuclear and chemical reactions, large-scale gravitational interactions, hydraulic flow, load deformation, and physiological systems. Computer graphics are nowhere so visible as in the entertainment industry, which uses them to create the interactive animations of video games and the special effects in motion pictures. Computers have also come into increasing use in commercial illustration and in the digitalization of images for use in CD-ROM products, online services, and other electronic media.
Hypertext is also called Hyperlinking, the linking of related pieces of information by electronic connections in order to allow a user easy access between them. Hypertext is a feature of some computer programs that allow the user of electronic media to select a word from text and receive additional information pertaining to that word, such as a definition or related references within the text. In the article "whale" in an electronic encyclopedia, for example, a hypertext link at the mention of the blue whale enables the reader to access the article on that species merely by "clicking" on the words "blue whale" with a mouse. The hypertext link is usually denoted by highlighting the relevant word or phrase in text with a different font or colour. Hypertext links can also connect text with pictures, sounds, or animated sequences. Hypertext links between different parts of a document or between different documents create a branching or network structure that can accommodate direct, unmediated jumps to pieces of related information. The treelike structure of hyperlinked information contrasts with the linear structure of a print encyclopaedia or dictionary, for example, whose contents can be physically accessed only by means of a static, linear sequence of entries in alphabetical order. Hypertext links are, in a sense, text cross-references that afford instant access to their target pieces of information. Such links are most effective when used on a large array of information that is organized into many smaller, related pieces and when the user requires only a small portion of information at any one time. Hypertext has been used most successfully by the interactive multimedia computer systems that came into commercial use in the early 1990s. Text 13. Computer network Computer network is also called Network, two or more computers that are connected with one another for the purpose of communicating data electronically. Besides physically connecting computer and communication devices, a network system serves the important function of establishing a cohesive architecture that allows a variety of equipment types to transfer information in a near-seamless fashion. Two popular architectures are ISO Open Systems Interconnection (OSI) and IBM's Systems Network Architecture (SNA). Two basic network types are local-area networks (LANs) and wide-area (or long-haul) networks. LANs connect computers and peripheral devices in a limited physical area, such as a business office, laboratory, or college campus, by means of permanent links (wires, cables, fibre optics) that transmit data rapidly. A typical LAN consists of two or more personal computers, printers, and high-capacity disk-storage devices called file servers, which enable each computer on the network to access a common set of files. LAN operating system software, which interprets input and instructs networked devices, allows users to communicate with each other; share the printers and storage equipment; and simultaneously access centrally located processors, data, or programs (instruction sets). LAN users may also access other LANs or tap into wide area networks. LANs with similar architectures are linked by "bridges," which act as transfer points. LANs with different architectures are 1inked by "gateways," which convert data as it passes between systems. Wide-area networks connect computers and smaller networks to larger networks over greater geographic areas, including different continents. They may link the computers by means of cables, optical fibres, or satellites, but their users commonly access the networks via a modem (a device that allows computers to communicate over telephone lines). The largest wide-area network is the Internet,a collection of networks and gateways linking millions of computer users on every continent. Text 14. Computer security Computer security is the protection of computer systems and information from harm, theft, and unauthorized use. Computer hardware is typically protected by the same means used to protect other valuable or sensitive equipment, namely, serial numbers, doors and locks, and alarms. The protection of information and system access, on the other hand, is achieved through other tactics, some of them quite complExercise The security precautions related to computer information and access address four major threats: (1) theft of data, such as that of military secrets from government computers; (2) vandalism, including the destruction of data by a computer virus; (3) fraud, such as employees at a bank channeling funds into their own accounts; and (4) invasion of privacy, such as the illegal accessing of protected personal financial or medical data from a large database. The most basic means of protecting a computer system against theft, vandalism, invasion of privacy, and other irresponsible behaviours is to electronically track and record the access to, and activities of, the various users of a computer system. This is commonly done by assigning an individual password to each person who has access to a system. The computer system itself can then automatically track the use of these passwords, recording such data as which files were accessed under particular passwords and so on. Another security measure is to store a system's data on a separate device, or medium, such as magnetic tape or disks, that is normally inaccessible through the computer system. Finally, data is often encrypted so that it can be deciphered only by holders of a singular encryption key. Computer security has become increasingly important since the late 1960s, when modems (devices that allow computers to communicate over telephone lines) were introduced. The proliferation of personal computers in the 1980s compounded the problem because they enabled hackers (irresponsible computerphiles) to illegally access major computer systems from the privacy of their homes. The development of advanced security techniques continues to diminish such threats, though concurrent refinements in the methods of computer crime pose ongoing hazards. Text 15. Computer crime Computer crime is any crime that is committed by means of the special knowledge or expert use of computer technology. Computer crime became a serious problem with the proliferation of such technology in the late 20th century. Since the first reported case of computer abuse in 1958, computers have been involved in most types of crimes, including theft, burglary, larceny, fraud, embezzlement, extortion, sabotage, espionage, kidnapping, and murder. Computer systems themselves can be the targets of attack, as when a computer virus is surreptitiously introduced into a system to alter or destroy data. Breaking into private computer systems to destroy, steal, or alter information became easier once modems (devices that allow computers to communicate over telephone lines) were introduced in the 1960s. Technically expert computer hobbyists who use personal computers and modems to break into and tamper with computer systems are known as "hackers." Most serious computer crimes, however, are committed in the banking and financial-service industries, where money, credit, and other financial assets are recorded in electronic databases and are transmitted as signals over telephone lines. Persons with access to such systems may falsify or manipulate these records for their own purposes by, for example, illegally transferring money balances to their own accounts. Text 16. Computer virus Computer virus is a portion of a program code that has been designed to furtively copy itself into other such codes or computer files. It is usually created by a prankster or vandal to effect a nonutilitarian result or to destroy data and program code. A virus consists of a set of instructions that attaches itself to other computer programs, usually in the computer's operating system, and becomes part of them. In most cases, the corrupted programs continue to perform their intended functions but surreptitiously execute the virus's instructions as well. A virus is usually designed to execute when it is loaded into a computer's memory. Upon execution, the virus instructs its host program to copy the viral code into, or "infect," any number of other programs and files stored in the computer. The infection can then transfer itself to files and code on other computers through magnetic disks or other memory-storage devices, computer networks, or online systems. The replicating viruses often multiply until they destroy data or render other program codes meaningless. A virus may simply cause a harmless joke or cryptic message to appear on a computer user's video monitor each time he turns on his computer. A more damaging virus can wreak havoc on an extremely large computer system within a matter of minutes or hours, causing it to crash and thereby destroy valuable data.
|
||||
|
Последнее изменение этой страницы: 2016-06-22; просмотров: 862; Нарушение авторского права страницы; Мы поможем в написании вашей работы! infopedia.su Все материалы представленные на сайте исключительно с целью ознакомления читателями и не преследуют коммерческих целей или нарушение авторских прав. Обратная связь - 18.119.142.113 (0.009 с.) |

 Text 12. Hypertext
Text 12. Hypertext