Заглавная страница Избранные статьи Случайная статья Познавательные статьи Новые добавления Обратная связь FAQ Написать работу КАТЕГОРИИ: ТОП 10 на сайте Приготовление дезинфицирующих растворов различной концентрацииТехника нижней прямой подачи мяча. Франко-прусская война (причины и последствия) Организация работы процедурного кабинета Смысловое и механическое запоминание, их место и роль в усвоении знаний Коммуникативные барьеры и пути их преодоления Обработка изделий медицинского назначения многократного применения Образцы текста публицистического стиля Четыре типа изменения баланса Задачи с ответами для Всероссийской олимпиады по праву 
Мы поможем в написании ваших работ! ЗНАЕТЕ ЛИ ВЫ?
Влияние общества на человека
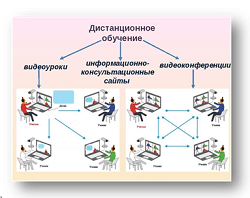
Приготовление дезинфицирующих растворов различной концентрации Практические работы по географии для 6 класса Организация работы процедурного кабинета Изменения в неживой природе осенью Уборка процедурного кабинета Сольфеджио. Все правила по сольфеджио Балочные системы. Определение реакций опор и моментов защемления |
II. Name the words using the definitionsСодержание книги
Поиск на нашем сайте
1. a set of jobs that are processed together on a computer. 2. existing or happening over a large area or among many people. 3. to make a substance containing harmful bacteria that can spread a disease. 4. the fact of sb/sth arriving, especially when it is not expected. 5. a person who has been attacked. 6. 7. to be free of sb/sth that has been annoying you. 8. the ability to understand or to do sth. 9. to do a piece of work. 10. that you must do because of the law, rules, etc. III. Read the text: "Types of viruses" A computer vims is a program able to create the copies which are not oblig atory coincide with an original and to incu lcate them in different objects of the computer systems, network, etc, and also to execute some destructive actions without user's knowing it. There is a great number of different classifications of these hurtful programs. Let us consider the most widespread classes of viruses. According to the habitat all viruses can be divided into four large groups. File viruses. These viruses were most widespread before appearance of the Internet. Today the harmful programs infect all types of executable objects of any operating system. In case with Windows batch files, drivers, executable files, dynamic libraries, etc, are in danger. At first virus writes down its code in a file - victim. As a result of this when the operating system addresses to it the control is transferred to the vims code, which can execute any actions set to it by a creator (to load into the main memory, to infect other programs, etc.) That's why if there is no special software on the user's computer, he can't guess about infection for a long time. Loadi ng viruses. These viruses infect not files but the loading sectors of diskettes and hard disk. A virus adds its code to one of the special programs which begin to be executed after computer switch on till the loading of the operating system. Thus, a virus gets the control and can execute certain actions, for example, to write down itself in the main memory. And only after it the operating system will be loaded. But viras.has already been in the memory and will be able to control its work, Macroviruses. These are the programs which are executed in languages built in different program systems. More frequently the files created by different components of Microsoft Office (Word, Excel, etc.) become the victims. Principle of their action is very' simple. A virus writes down itself in a DOT - file, which all global macros are in, part of which it s ubstitute s by itself. After that all files stored in this program will contain a macrovirus. Thus, it can execute a great number of different destructive actions up to the deleting of all documents. Net work viruses. The main feature of these viruses is the ability to work with different network protocols. The most spread in our time are internet worms. These viruses use an e-mail for the work, "hooking" to the letter. There are three groups of viruses based on their destructive action. The first group is harmless. The second group is dangerous. Viruses which can result in certain failures in work of the operating system. T he third group is critical. These viruses can destroy certain or all iivformation being on a hard disk, change system information, put out of order the operating system, etc. Let's examine the classification of viruses based on the features of th algorithms. R esident vi r uses. They are the varieties of file and loading viruses. I they are the most dangerous variety. After the start of the infected file tl write down their sieves into the main memory and keep their working capac up to the restart of a computer. In most cases it is impossible to get rid resident viruses by the deleting of all infected appendixes, gt els - viruses. These viruses are able to hide their presence in system. Finding out their presence is very difficult. Stcls - viruses use differ ways to secure invisibility. Next variant is the mosl widespread. This vi consists of two parts. One of them is the resident. It is constantly in memory a computer. If the operating system addresses the infected file a '-reside intercepts this ap peal and deletes the code of virus from a file. The appendi: "clean". But when it completes tire work "the resident" again infects it. P olymorphic viruses. The feature of these viruses is the ability to chai their own code. It is done in order to mislead the anti - virus programs of using "masks" (code fragments typical of viruses). There are two types polymorphic viruses. The first only codes its own "body" with the inconst key and casual set of commands of decoder. The second group is more diffic The viruses related to it can rewrite the code, in fact, they are programmers, IV. Understanding the text Decide whether the following statements are true or false referring to the information in the text. Then make the necessary chan so that the false statements become true. 1. All viruses are divided into three main groups according to the habii destructive action, features of their algorithms. 2. File viruses are harmless. 3. Polymorphic viruses can easily be destroyed 4. Stels - viruses can rewrite their code. 5. The viruses can destroy certain or all information being on a hard di 6. The most spread resident virus is worms. 7. File viruses infect not files but the loading sectors of diskettes and 1 disks. 8. Loading viruses can write down themselves into the main memory. 9. Resident viruses are the variation of macroviruses. 10. There are three types of polymorphic viruses. V. Match A with В
VI. Answer the questions 1. How many virus classifications do you know? 2. What are the most destructive types of viruses? 3. What type of viruses can hide its presence in the system? 4. What is the name of the most spread network viruses'? 5. What type of viruses is the programmer? 6. Is the feature of polymorphic viruses to change their own code or to hide their presence in the system? 7. Viruses can destroy all information, can't they? 8. Why is it very difficult to find out the stcls - viruses presence? 9. Arc the resident viruses the varieties of macroviruscs? 10. How many groups have polymorphic viruses? What are they?
|
|||||||||||||||||||||||||||||||
|
Последнее изменение этой страницы: 2017-02-10; просмотров: 197; Нарушение авторского права страницы; Мы поможем в написании вашей работы! infopedia.su Все материалы представленные на сайте исключительно с целью ознакомления читателями и не преследуют коммерческих целей или нарушение авторских прав. Обратная связь - 3.12.147.12 (0.006 с.) |

 to stop sb/sth which is going from one place to another from arriving
to stop sb/sth which is going from one place to another from arriving