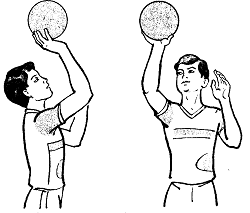
Заглавная страница Избранные статьи Случайная статья Познавательные статьи Новые добавления Обратная связь FAQ Написать работу КАТЕГОРИИ: ТОП 10 на сайте Приготовление дезинфицирующих растворов различной концентрацииТехника нижней прямой подачи мяча. Франко-прусская война (причины и последствия) Организация работы процедурного кабинета Смысловое и механическое запоминание, их место и роль в усвоении знаний Коммуникативные барьеры и пути их преодоления Обработка изделий медицинского назначения многократного применения Образцы текста публицистического стиля Четыре типа изменения баланса Задачи с ответами для Всероссийской олимпиады по праву 
Мы поможем в написании ваших работ! ЗНАЕТЕ ЛИ ВЫ?
Влияние общества на человека
Приготовление дезинфицирующих растворов различной концентрации Практические работы по географии для 6 класса Организация работы процедурного кабинета Изменения в неживой природе осенью Уборка процедурного кабинета Сольфеджио. Все правила по сольфеджио Балочные системы. Определение реакций опор и моментов защемления |
Here are some reasons why some people attend or avoid attending conferences. Ask your groupmate if he/she would like to attend a conference. Support your opinions using the reasons given below.Содержание книги
Поиск на нашем сайте
Listening 1.Match the words with their definitions.
Listen to Sarah Wood, an ICT teacher, explaining why people should attend conferences. What are three main reasons for attending a conference? What is the most important one according to Sarah Wood? Listen to the first part of the recording and say why learning is important. Complete the extract with the words from the box. Listen to the second part of the recording and check your answers.
What is even more important than ___1)___ is the excitement about your work and the career that builds when you are at a conference. If you are presenting you get the opportunity to ___2)___ what you are doing in a formal way, which promotes ___3)___ afterwards. When you listen to others, your practices, assumptionsand beliefs may be challenged or ___4)___. Critically thinking about what you hear can help you pick up or ___5)___ new ideas. New ideas will excite you and ___6)___ your work. I just got back from the most amazing conference about innovations in online learning and am very ___7)____ to apply the tips and tricks I learned while I was there to these videos and my teaching. It was ___8___ to get away and be immersed in the atmosphere of the conference. 5. Listen to the third part of the recording. Which definition best describes networking?
a) a group of people learning new subjects together; b)the process of trying to meet new people who might be useful to you in your job, often through social activities; c) a large number of people that have a connection with each other and work together as a system.
There are a few more opinions about the importance of scientific conferences. a) Look through them and continue the list of reasons given in task 2. Put down the most important ones.
b) Work in pairs. Persuade your groupmate to attend a conference. Name at least 3 reasons. Use the ideas from the list. To add information you can use: Furthermore, Moreover, Similarly, What is more, Also, etc. Module 3 Multifunctional Words Признаки распознавания функций и значений since
XIX. Define the functions and meanings of the multifunctional word since. Name its features as a subordinating conjunction of the complex sentence. 1.This method of control greatly improves flexibility in use since it takes advantage of the high speed of the system. 2. The advent of the Internet and the World Wide Web caused a revolution in the availability of information not seen since the invention of the printing press.3. Since each particle may be in either of two spin states, or in both, calculations can be simultaneously done for both states. 4. The actual operating program is normally stored in read-only memory (ROM) or in a permanent logic array, since the user does not need to change this program. 5. Since all operations must be synchronized—that is, they must work together in the correct sequence—a crystal oscillator clock is also installed to regulate the timing. 7. Since its invention in two basic forms in the late 1980s, flash memory has become standard for portable devices such as digital cameras, cellular telephones, PDAs, MP3 players, and video-game machines. XX. Give the Russian equivalents of the following sentences. 1. Microprocessor applications have grown rapidly since the 1970s. 2. We say that an object at rest has no kinetic energy since its velocity is zero. 3. Since the early 1980s, increasingly sophisticated tools have been built to aid the software developers. 4. Since the inception of computer memory, the capacity of both internal and external memory devices has grown steadily. 5. Integrated circuit memory quickly displaced core and has been the dominant technology for internal memory ever since. 6. Since computers have only a limited amount of memory, software designers must limit the number of features they include in a program. 7. Java has since become popular for writing applications for the Internet.8. More than a hundred years have passed since A.S.Popov demonstrated his radio receiver.
Text 1. There are many benefits from an open system like the Internet, but one of the risks is that we are often exposed to hackers, who break into computer systems just for fun, to steal information, or to spread viruses. So how do we go about making our online transactions secure? 2. Security is crucial when you send confidential information online. Consider, for example, the process of buying a book on the Web. You have to type your credit card number into an order form which passes from computer to computer on its way to the online bookstore. If one of the intermediary computers is infiltrated by hackers, your data can be copied. To avoid risks, you should set all security alerts to high on your web browser. If you use online banking services, make sure they use digital certificates – files that are like digital identification cards and that identify users and web servers. Also be sure to use a browser that is compliant with SSL (Secure Sockets Layer), a protocol which provides secure transactions. 3. Similarly, as your email travels across the Net, it is copied temporarily onto many computers in between. This means that it can be read by people who illegally enter computer systems. The only way to protect a message is to put it in a sort of virtual envelope – that is to encode it with some form of encryption. 4. Private networks can be attacked by intruders who attempt to obtain information such as Social Security numbers, bank accounts or research and business reports. To protect crucial data, companies hire security consultants who analyse the risks and provide solutions. The most common methods of protection are passwords for access control, firewalls, and encryption and decryption systems. Encryption changes data into a secret code so that only someone with a key can read it. 5. Malware (malicious software) are programs designed to infiltrate or damage your computer, for example viruses, worms, Trojans and spyware. A virus can enter a PC via a disk drive – if you insert an infected disc – or via the Internet. A worm is a self-copying program that spreads through email attachments; it replicates itself and sends a copy to everyone in an address book. A Trojan horse is disguised as a useful program; it may affect data security. Spyware collects information from your PC without your consent. If you want to protect your PC, don’t open email attachments from strangers and take care when downloading files from the Web. Remember to update your anti-virus software as often as possible, since new viruses are being created all the time. Reading 1. Read the definitions of these words. Guess their meaning. break into - to enter illegally compliant – compatible, able to exist together spread - to distribute or be distributed over an area or region infiltrate –to pass undetected avoid - to prevent from happening consent- permission crucial - decisive, very important disguise - make (something) unrecognizable by altering its appearance
|
|||||||||||||||||||||||||||||||
|
Последнее изменение этой страницы: 2016-08-01; просмотров: 142; Нарушение авторского права страницы; Мы поможем в написании вашей работы! infopedia.su Все материалы представленные на сайте исключительно с целью ознакомления читателями и не преследуют коммерческих целей или нарушение авторских прав. Обратная связь - 18.225.72.181 (0.006 с.) |