Заглавная страница Избранные статьи Случайная статья Познавательные статьи Новые добавления Обратная связь FAQ Написать работу КАТЕГОРИИ: ТОП 10 на сайте Приготовление дезинфицирующих растворов различной концентрацииТехника нижней прямой подачи мяча. Франко-прусская война (причины и последствия) Организация работы процедурного кабинета Смысловое и механическое запоминание, их место и роль в усвоении знаний Коммуникативные барьеры и пути их преодоления Обработка изделий медицинского назначения многократного применения Образцы текста публицистического стиля Четыре типа изменения баланса Задачи с ответами для Всероссийской олимпиады по праву 
Мы поможем в написании ваших работ! ЗНАЕТЕ ЛИ ВЫ?
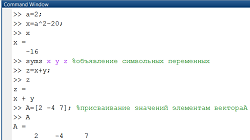
Влияние общества на человека
Приготовление дезинфицирующих растворов различной концентрации Практические работы по географии для 6 класса Организация работы процедурного кабинета Изменения в неживой природе осенью Уборка процедурного кабинета Сольфеджио. Все правила по сольфеджио Балочные системы. Определение реакций опор и моментов защемления |
Read the text and translate it: Computer crimeСодержание книги Поиск на нашем сайте Computer crimes encompass unauthorized or illegal activities perpetrated via computer as well as the theft of computers and other technological hardware. As firms of all sizes, industrial orientation, and geographic location increasingly rely on computers to operate, concerns about computer crime have also risen, in part because the practice appears to be thriving despite the concerted efforts of both the law enforcement and business communities to stop it. But computer experts and business consultants alike note that both international corporations and modest family-owned businesses can do a great deal to neutralize computer "viruses" and other manifestations of computer crime. Many analysts believe, however, that small business owners are less likely to take steps to address the threat of computer crime than are larger firms. Indeed, many small businesses admit that they are passive about the threat because of costs associated with implementing safeguards and the perception that computer "hackers" and other threats are far more likely to pick on bigger companies. But as Tim McCollum flatly stated in Nation's Business, "companies increasingly are falling prey to hackers, computer thieves, software viruses, and, in particular, unauthorized and often illegal activities by their own employees. Early use of the term "hacker" was applied to computer hobbyists who spent their spare time creating video games and other basic computer programs. However, this term acquired a negative connotation in the 1980s when computer experts illegally accessed several high-profile databanks. Databases at the Los Alamos National Laboratory (a center of nuclear weapons research) and the Sloan-Kettering Cancer Center in New York City were among their targets. The introduction of relatively inexpensive personal computers and modems helped make this pastime affordable; the use of regular telephone lines as accessways made it possible. Computer crimes perpetrated by outsiders are a major threat too, of course, but whereas employees often abscond with sensitive information or attempt to benefit financially when engaging in illegal activities, outsiders are more likely to engage in behavior that is simply destructive (i.e., computer viruses). Some security experts believe that the continued threat of outside "hackers" is due at least in part to the growing number of employees who engage in "telecommuting" via modem and the swelling ranks of company networks hooked to the Internet. These connections can be used to infiltrate computer systems. The damage wreaked by outside intruders can be significant and wide-ranging. The most common outside threat to a business's computer network is the virus. Indeed, the National Computer Security Association (NCSA) estimated that in 1996, two out of three U.S. companies were affected by one or more of the estimated 16,000 computer viruses that were floating around the country at that time. Viruses infect your machine by attaching themselves to programs, files, and start-up instructions. There are two main types of computer viruses: macro and binary. Macro viruses are written to attack a specific program…. Binary viruses are either actual programs designed to attack your data or attach themselves to program files to do similar destruction. Binary viruses are the ones to be concerned with; they can reformat your hard drive, wipe out data and stop your operating system from working. The best way to fight these bugs is to avoid them—but in today's word of Internet downloads and e-mail file exchanges, this is an impossible task. Computer security is concerned with preventing information stored in or used by computers from being altered, stolen, or used to commit crimes. The field includes the protection of electronic funds transfers, proprietary information (product designs, client lists, etc.), computer programs, and other communications, as well as the prevention of computer viruses. Post-text exercises: 1. Put the words in the right order to make a sentence: 1. The, the, a, most, outside, threat, computer, is, to, common, virus.2 Viruses, to, written, attack a, are, specific, macro, program. 3. Two, there, are, main, viruses, types, computer, of. 4. Hobbyists, was, "hacker", video, who, spare, their, time, spent, creating, games. 5. By, crimes, computer, outsiders, perpetrate. 6. Best, is, way, the, fight, bugs, to, to, avoid, these, them. 7. Binary, your, viruses, actual, designed, are, either, to, attack, programs, data. 8. Viruses, infect, to, by, attaching, programs, themselves, your, machine. 9. Computer, is, stored, with, concerned, information, security, preventing, in. 10. NCSA, computer, estimated, three, two, U.S. companies, were, that, affected, out, of, by, viruses. 2. Fill in the blanks with the following words: Video, virus, "hackers", viruses, program, to attack, affected, machine, information 1. The most common outside threat to a business's computer network is the... 2. Macro viruses are written to attack a specific … 3. Binary … can reformat your hard drive. 4. "hackers " are hobbyists who spent their spare time creating … games. 5. Viruses infect your …by attaching themselves to programs. 6. Binary viruses are either actual programs designed … your data. 7. Some security experts believe that the continued threat of outside … is due at least in part to the growing number of employees.8. Computer security is concerned with preventing … stored in or used by computers from being altered, stolen, or used to commit crimes.9. The National Computer Security Association estimated that in 1996, two out of three U.S. companies were … by one or more of the estimated 16,000 computer viruses. 3. Complete the following sentences using active vocabulary: 1. Computer crimes perpetrated by outsiders are … 2. The most common outside threat to … 3. "hackers" were hobbyists who spent their spare time creating …4. Some security experts believe that the continued threat of outside "hackers" is … 5. Viruses infect your machine by… 6. Binary viruses can reformat your …7. Some security experts believe that the continued threat of outside "hackers" is due at least in… 8. The damage wreaked by outside intruders can be … 9. The National Computer Security Association (NCSA) estimated that in 1996, two out of three U.S. companies were affected by … 4. Say if the following statements are true or false: 1. Binary viruses can’t reformat your hard drive. 2. The damage wreaked by outside intruders can be significant and wide-ranging. 3. Viruses infect your video games. 4. Macro viruses are written to attack a specific program. 5. "hacker" is a legal activity. 6. There are three main types of computer viruses. 7. Some security experts believe that the continued threat of outside "hackers" is due at least in part to the growing number of employees. 8. Computer crime, or cybercrime, is only national phenomenon. 9. The National Computer Security Association estimated that in 1996, two out of three U.S. companies were affected by one or more of the estimated 16,000 robots. 5. Answer the following questions: 1. What is the most common outside threat to a business's computer network? 2. How many types of computer viruses are there? 3. Who is a "hacker"? 4.How do you defend your computer?5. What viruses can reformat your hard drive? 6. How do viruses infect your machine? 7. What are macro viruses written to? 8. What can reformat your hard drive? 9. When did the National Computer Security Association estimate that two out of three U.S. companies were affected by computer viruses? 6. Match the first part (1-9) of the sentence with the second part (a-i): 1. Spam is … 2. A computer virus is … 3 Computer fraud is … 4. Cyberstalking is … 5. Malware is … 6. A hard disk drive (HDD) is … 7. A way of representing text or computer processor instructions by the use of … 8. The Internet is … 9. Cyberterrorism is … a) … a non-volatile, random access device for digital data. b) … unlawful to varying degrees. c) …software designed to secretly access a computer system without the owner's informed consent. d) … any dishonest misrepresentation of fact intended to let another to do or refrain from doing something which causes loss. e) … the binary number system's two-binary digits 0 and 1. f)… the use of the Internet to stalk or harass an individual or an organization. g) … a computer program that can copy itself and infect a computer. h) … a global system of interconnected computer networks that use the standard Internet Protocol Suite (TCP/IP) to serve billions of users worldwide. i) … a phrase used to describe the use of Internet based attacks in terrorist activities.
|
||
|
Последнее изменение этой страницы: 2016-04-18; просмотров: 484; Нарушение авторского права страницы; Мы поможем в написании вашей работы! infopedia.su Все материалы представленные на сайте исключительно с целью ознакомления читателями и не преследуют коммерческих целей или нарушение авторских прав. Обратная связь - 216.73.216.102 (0.009 с.) |