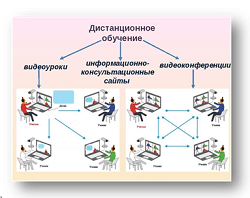
Заглавная страница Избранные статьи Случайная статья Познавательные статьи Новые добавления Обратная связь FAQ Написать работу КАТЕГОРИИ: ТОП 10 на сайте Приготовление дезинфицирующих растворов различной концентрацииТехника нижней прямой подачи мяча. Франко-прусская война (причины и последствия) Организация работы процедурного кабинета Смысловое и механическое запоминание, их место и роль в усвоении знаний Коммуникативные барьеры и пути их преодоления Обработка изделий медицинского назначения многократного применения Образцы текста публицистического стиля Четыре типа изменения баланса Задачи с ответами для Всероссийской олимпиады по праву 
Мы поможем в написании ваших работ! ЗНАЕТЕ ЛИ ВЫ?
Влияние общества на человека
Приготовление дезинфицирующих растворов различной концентрации Практические работы по географии для 6 класса Организация работы процедурного кабинета Изменения в неживой природе осенью Уборка процедурного кабинета Сольфеджио. Все правила по сольфеджио Балочные системы. Определение реакций опор и моментов защемления |
Give the Russian equivalents of the following words and word combinationsСодержание книги
Поиск на нашем сайте
To be concerned in maintaining of general safety of network, open a set of new opportunities, provide the creation of information resources, the solution of the wide spectrum of problems, take info account, direct on information safety assurance, confirmation, intercept, be not capable, safety threat, requirement, increased information security level, preferable, vulnerable network components, narrowness of the solved problem.
GRAMMAR REVISION Change the active form into the passive one. 1. They gave up the search after three hours. 2 They ought to have pointed that out to me at the very beginning. 3. No one brought up that question at the meeting. 4. Somebody should look into the matter. 5. It was clear that toe parents had brought toe child up well. 6. We had to put off our visit until later. 7. I was shocked to hear that someone had broken into your house. 8. Don't speak until someone speaks to you. 9. His bank manager turned down his request for a loan. 10. You must account for every penny you spent. 11. Someone hasn't stuck this toe stamp on very firmly. 12 Events will bear out the truth of what I'm saying. 13. An official held us up at the Customs for half an hour. 14.How can we bring about toe desired result? 15. He hates people making fun of him. Complete the sentences using the Passive Voice 1.The new washing machines (turn out) at tе rate of fifty a day. 2.When her husband died, she naturally assumed that she (provide for) 3. We've had to move into a hotel while (lie house we've just bought (do up). 4.The employee was assured of his (take on) again as soon as work was available. 5.Richard always (tell off) for careless mistakes nowadays. 6.The agreement had to (draw up) in the presence of two witnesses. 7. Some Heads of Government now fear that negotiations (break off) before a settlement is reached. 8.The chairman of thе board of directors assured shareholder that the matter of the deficiency (look into) by the time the next meeting was held. 9. He felt he (let down) badly by his best friend. 10. The search party had little idea where to start looking the climber's tracks (blot out) by a recent snowstorm. Use the Passive Voice in the following sentences. 1. (Everyone) knows this fact very well. 2. (They) opened the theatre only last month 3. (People) will soon forget it. 4. (You) must write the answers in ink. (Someone) has taken two of my books. 5. (We) have already filled the vacancy.6.What should (one) do in such case? 7. Did (they) say anything interesting? 8. Did (no one) ever make the situation clear to you? (One) should keep milk in a refrigerator.10.I don't think (anyone) can do it. 11. (They) would undoubtedly have killed him if he hadn't promised to cooperate. 12. (You) must finish the work by 7.11. (They) are no\v manufacturing this type of computer in many countries.14. (No one) could possibly have known the secret.
UNIT 3 Read and translate the text. TEXT A Substitution ciphers A substitution cipher is one in which the units of the plaintext (usually letters or numbers) are replaced with other symbols or groups of symbols. The actual order of the units of the plaintext is not changed. The simplest substitution cipher is one where the alphabet of the cipher is merely a shift of the plaintext alphabet, for example, A might be encrypted as В, С as D and so forth. Of this type of cipher, the most well-known is Caesar cipher, used by Julius Caesar in which A becomes D etc. It is easy to guess that cyclical-shift substitution ciphers of this sort are not at all secure because individual letter frequencies are left completely intact. Product ciphers. In the days of manual cryptography i. e. without the aid of the computer product ciphers were a useful device for the cryptographer and double transposition ciphers on keyword-based matrices were, in fact, widely used.There was also some use of a particular class of product ciphers called fractionation systems. In a fracti'onation system a substitution is first made from symbols in the plaintext to multiple symbols (usually pairs, in which case the cipher is called bilateral cipher) in the ciphertext, which is then superencrypted by a transposition. Block ciphers. Generally, ciphers transform pieces of the plaintext of a fixed size into ciphertext. In older, manual systems, these pieces were usually single letters or characters (or sometimes, as in the Playfair cipher, digraphs), since these were the largest units that could be easily encrypted or decrypted by hand. Although systems which operated on sets of three characters and other, larger groups of numbers, were proposed and understood to potentially be more secure they were implemented because of the extra difficulty in the manual encryption or decryption process. In modern, single key cryptography however, the units of information can be much larger. A block cipher is a type of symmetric-key encryption algorithm that changes a fixed-length block of the plain text into the same length of cipher text. The encryption works by means of a key. Decryption is a simply the reverse of the encryption process using the same secret key. The fixed length is called the block size and for modern block ciphers is usually 64 bits. As processors become more sophisticated, however, it is likely that this"block size will increase to 128 bits. Stream ciphers. A stream cipher also breaks the plaintext into units, this time it is normally a single character. It then encrypts the n* unit of the plaintext with the в* unit of the key stream. Stream ciphers can be designed to be exceptionally fast, much faster than any block cipher. While the encryption of any particular plaintext with a block cipher will result in the same ciphertext when the same key is used. With a stream cipher, the transformation of the smaller plaintext units will vary, depending on when they are encountered during the encryption process. A stream cipher generates what is known as a keystream — a sequence of bits, which is used as a key.The encryption process involves combining the keystream with the plaintext. The keystream can be generated in two ways. 1. Independent of the plaintext and ciphertext (this yields what is known as a synchronous stream cipher). 2. Depending on the data and its encryption(in which case the stream cipher is said to be self-synchronising). In a chosen plaintext attack the cryptanalyst has the capability to find the ciphertext corresponding to an arbitrary plaintext message of his or her own choosing. The likelihood of this type of attack being possible is not much. Codes which can survive this attack are considered to be very secure. In a chosen ciphertext attack the cryptanalyst can choose an arbitrary cipher-text and find the corresponding decrypted plaintext. This attack can be used in public key systems, where it may reveal the private key. In an adaptive chosen plaintext attack the cryptoanalyst can determine the ciphertext of chosen plaintexts in an iterative process based on previous results. This is the general name for a method of attacking product ciphers called "differential cryptoanalysis".
Text B Types of cryptoanalysis There are several distinct types of cryptoanalytic attack. The type used depends on the type of cipher and how much information the cryptoanalyst has. Types of cryptoanalytic attacks. A standard cryptoanalytic is to determine the key which maps a known plaintext to a known ciphertext.This plaintext can be known because it is standard or because it is guessed. If the plaintext segment is guessed it is unlikelely that its exact position is known however a message is generally short enough for a cryptoanalyst to try all possible positions in parallel. In some systems a known cipher-text-plaintext pair will compromise the entire system however a strong encryption algorithm will be unbreakable under this type of attack. A brute force attack requires a large amount of computing power and a large amount of time to run. It consists of trying all possibilities in a logical manner until the correct one is found. For the majority of the encryption algorithms a brute force attack is impractical due to the large number of possibilities. Another type of brute force attack is a dictionary attack. This essentially involves running through a dictionary of words in the hope that the key (or the plaintext) is one of them. This type of attack is often used to determine passwords since people usually use easy to remember words. In a ciphertext only attack the cryptanalyst has only the encoded message from which to determine the plaintext, with no knowledge whatsoever of the actual message. A ciphertext only attack is presumed to be possible, if not easy. In fact, an encryption techniques resistance to a ciphertext only attack is considered the basis for its cryptographic security.
COMPREHENSION CHECK Answer the questions 1. What is substitution cipher? 2. What examples of the simplest substitution ciphers can you give? 3. What is fractionation system? 4. What is block cipher? 5. Characterize stream cipher. 6. What are the ways to generate the keystream? 7. Define the types of cryptoanalysis.
|
||||
|
Последнее изменение этой страницы: 2016-12-10; просмотров: 1086; Нарушение авторского права страницы; Мы поможем в написании вашей работы! infopedia.su Все материалы представленные на сайте исключительно с целью ознакомления читателями и не преследуют коммерческих целей или нарушение авторских прав. Обратная связь - 3.144.98.61 (0.007 с.) |