Заглавная страница Избранные статьи Случайная статья Познавательные статьи Новые добавления Обратная связь КАТЕГОРИИ: ТОП 10 на сайте Приготовление дезинфицирующих растворов различной концентрацииТехника нижней прямой подачи мяча. Франко-прусская война (причины и последствия) Организация работы процедурного кабинета Смысловое и механическое запоминание, их место и роль в усвоении знаний Коммуникативные барьеры и пути их преодоления Обработка изделий медицинского назначения многократного применения Образцы текста публицистического стиля Четыре типа изменения баланса Задачи с ответами для Всероссийской олимпиады по праву 
Мы поможем в написании ваших работ! ЗНАЕТЕ ЛИ ВЫ?
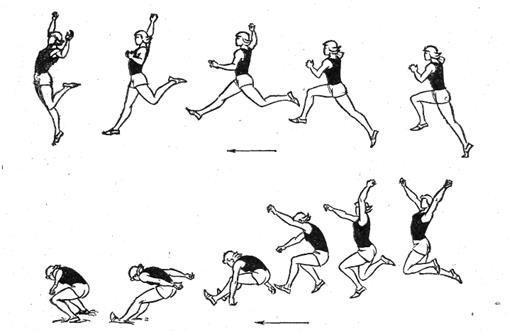
Влияние общества на человека
Приготовление дезинфицирующих растворов различной концентрации Практические работы по географии для 6 класса Организация работы процедурного кабинета Изменения в неживой природе осенью Уборка процедурного кабинета Сольфеджио. Все правила по сольфеджио Балочные системы. Определение реакций опор и моментов защемления |
Policy: Depending on limitations of the communications provider, the
call trace feature will be enabled globally to allow employees to activate the trap-and-trace feature when the caller is suspected of being an attacker.
Explanation/Notes: Employees must be trained on call trace usage and the appropriate circumstances when it should be used. A call trace should be initiated when the caller is clearly attempting to gain unauthorized access to corporate computer systems or requesting Sensitive information. Whenever an employee activates the call trace feature, immediate notification must be sent to the Incident Reporting Group.
3-9 Automated phone systems Policy." If the company uses an automated phone answering system, the system must be programmed so that telephone extensions are not announced when transferring a call to an employee or department.
Explanation/Notes: Attackers can use a company's automated telephone system to map employee names to telephone extensions. Attackers can then use knowledge of those extensions to convince call recipients that they are employees with a right to insider information.
3-10 Voice mailboxes to become disabled after successive invalid access attempts Policy: Program the corporate telephone system to lock out any voice mail account whenever a specified number of successive invalid access attempts have been made.
Explanation/Notes." The Telecommunications administrator must lock out a voice mailbox after five successive invalid attempts to log in. The administrator must then reset any voice mail lockouts manually.
3-11 Restricted telephone extensions Explanation/Notes:While use of this policy will block most attempts by amateur social engineers to reach their likely targets, it should be noted that a determined attacker will sometimes be able to talk an employee into calling the restricted extension and asking the person who answers the phone to call the attacker, or simply conference in the restricted extension. During security training, this method of tricking employees into assisting the intruder should be discussed to raise employee awareness about these tactics.
Miscellaneous 4-1 Employee badge design Policy: Employee badges must be designed to include a large photo that can be recognized from a distance.
Explanation/Notes: The photograph on corporate ID badges of standard design is, for security purposes, only slightly better than worthless. The distance between a person entering the building and the guard or receptionist who has the responsibility to check identification is usually great enough that the picture is too small to recognize when the person walks by. For the photo to be of value in this situation, a redesign of the badge is necessary.
4-2 Access rights review when changing position or responsibilities Policy: Whenever a company employee changes positions or is given increased or decreased job responsibilities, the employee's manager will notify IT of the change in the employee's responsibilities so that the appropriate security profile can be assigned.
Explanation/Notes: Managing the access rights of personnel is necessary to limit disclosure of protected information. The rule of least privilege will apply: The access rights assigned to users will be the minimum necessary to perform their jobs. Any requests for changes that result in elevated access rights must be in accordance with a policy on granting elevated access rights.
The worker's manager or the human resources department will have the responsibility of notifying the information technology department to properly adjust the account holder's access rights as needed.
4-3 Special identification for non employees Policy: Your company should issue a special photo company badge to trusted delivery people and non employees who have a business need to enter company premises on a regular basis.
Explanation/Notes: Non employees who need to enter the building regularly (for example, to make food or beverage deliveries to the cafeteria, or to repair copying machines or make telephone installations) can pose a threat to your company. In addition to issuing identification to these visitors, make sure your employees are trained to spot a visitor without a badge and know how to act in that situation.
4-4 Disabling computer accounts for contractors Policy: Whenever a contractor who has been issued a computer account has completed his or her assignment, or when the contract expires, the responsible manager will immediately notify the information technology
department to disable the contractor's computer accounts, including any accounts used for database access, dial-up, or Internet access from remote locations. Explanation/Notes: W-hen a worker's employment is terminated, there is a danger that he or she will use knowledge of your company's systems and procedures to gain access to data. All computer accounts used by or known to the worker must be promptly disabled. This includes accounts that provide access to production databases, remote dial-in accounts, and any accounts used to access computer-related devices.
4-5 Incident reporting organization Explanation/Notes: By centralizing the reporting of suspected security incidents, an attack that may otherwise have gone unnoticed can be detected. In the event that systematic attacks across the organization are detected and reported, the incident reporting organization may be able to determine what the attacker is targeting so that special efforts can be made to protect those assets.
Employees assigned to receive incident reports must become familiar with social engineering methods and tactics, enabling them to evaluate to reports and recognize when an attack may be in progress.
4-6 Incident reporting hotline Policy: A hotline to the incident reporting organization or person, which may consist of an easy-to-remember phone extension, must be established.
Explanation/Notes: When employees suspect that they are the target of a social engineering attack, they must be able to immediately notify the incident reporting organization. In order for the notification to be timely, all company telephone operators and receptionists must have the number posted or otherwise immediately available to them.
A company-wide early warning system can substantially aid the organization in detecting and responding to an ongoing attack. Employees must be sufficiently well trained that one who suspects he or she has been the target of a social engineering attack will immediately call the incident reporting hotline. In accordance with published procedures, the incident
reporting personnel will immediately notify the targeted groups that an intrusion may be in progress so personnel will be on alert. In order for the notification to be timely, the reporting hotline number must be widely distributed throughout the company.
4-7 Sensitive areas must be secured Policy: A security guard will screen access to sensitive or secure areas and should require two forms of authentication.
Explanation/Notes: One acceptable form of authentication uses a digital electronic lock that requires an employee to swipe his employee badge and enter an access code. The best method to secure sensitive areas is to post a security guard who observes any access-controlled entry. In organizations where this is not cost-effective, two forms of authentication should be used to validate identity. Depending on risk and cost, a biometric-enabled access card is recommended.
4-8 Network and phone cabinets Policy: Cabinets, closets, or rooms containing network cabling, phone wiring, or network access points must be secured at all times.
Explanation/Notes: Only authorized personnel will be permitted access to telephone and network closets, rooms, or cabinets. Any outside maintenance people or vendor personnel must be positively identified using the procedures published by the department responsible for information security. Access to phone lines, network hubs, switches, bridges, or other related equipment could be used by an attacker to compromise computer and network security.
4-9 Intracompany mail bins Policy: Intracompany mail bins must not be located in publicly accessible areas.
Explanation/Notes: Industrial spies or computer intruders who have access to any intracompany mail pickup points can easily send forged authorization letters or internal forms that authorize personnel to release Confidential information or to perform.an action that assists the attacker. Additionally, the attacker can mail a floppy disk or electronic media with instructions to install a software update, or open a file that has embedded macro commands that serve the intruder's objectives. Naturally, any request received by intracompany mail is assumed to be authentic by the party who receives it.
4-10 The company bulletin board
Policy: Bulletin boards for the benefit of company workers should not be posted in locations where the public has access.
Explanation/Notes: Many businesses have bulletin boards where private company or personnel information is posted for anyone to read. Employer notices, employee lists, internal memorandums, employee home contact numbers listed in advertisements, and other, similar information are frequently posted on the board.
Bulletin boards may be located near company cafeterias, or in close proximity to smoking or break areas where visitors have free access. This type of information should not be made available to visitors or the public.
4-1 1 Computer center entrance Policy: The computer room or data center should be locked at all times and personnel must authenticate their identity prior to entering. Explanation/Notes:Corporate security ought to consider deploying an electronic badge or access card reader so all entries can be electronically logged and audited.
4-12 Customer accounts with service providers Explanation/Notes: Utility companies and many other vendors allow customers to set up a password on request; the company should establish passwords with all vendors that provide mission-critical services. This policy is especially critical to telecommunication and Internet services. Any time critical services can be affected, a shared secret is necessary to verify that the caller is authorized to place such orders. Note, too, identifiers such as social security number, corporate taxpayer identification number,
4-1 3 Departmental contact person Policy: Your company may institute a program under which each department or workgroup assigns an employee the responsibility of acting as a point contact so that any personnel can easily verify the identity of unknown persons claiming to be from that department. For example, the help desk may contact the departmental point person to verify the identity of an employee who is requesting support.
Explanation/Notes: This method of verifying identity reduces the pool of employees who are authorized to vouch for employees within their department when such employees request support such as resetting passwords or other computer account-related issues.
Social engineering attacks are successful in part because technical support personnel are pressed for time and do not properly verify the identity of requesters. Typically support staff cannot personally recognize all authorized personnel because of the number of employees in larger organizations. The point-person method of vouching limits the number of employees that technical support staff need to be personally familiar with for verification purposes.
4-14 Customer passwords Policy: Customer service representatives shall not have the ability to retrieve customer account passwords.
Explanation/Notes: Social engineers frequently call customer service departments and, under a pretext, attempt to obtain a customer's authentication information, such as the password or social security number. With this information, the social engineer can then call another service representative, pretend to be the customer, and obtain information or place fraudulent orders.
To prevent these attempts from succeeding, customer service software must be designed so that representatives can only type in the authentication information provided by the caller, and receive a response from the system indicating whether the password is correct or not.
4-1 5 Vulnerability testing Policy: Notification of company use of social engineering tactics to test security vulnerabilities is required during security awareness training and employee orientation.
Explanation/Notes:Without notification of social engineering-penetration testing, company personnel may suffer embarrassment, anger, or other emotional trauma from the use of deceptive tactics used against them by other employees or contractors. By placing new hires on notice during the orientation process that they may be subject to this testing, you prevent such conflict.
4-16 Display of company Confidential information Policy: Company information not designated for public release shall not be displayed in any publicly accessible areas.
Explanation/Notes: In addition to Confidential product or procedure information, internal contact information such as internal telephone or employee lists, or building rosters that contain a list of management personnel for each department within the company must also be kept out of view.
4-17 Security awareness training Policy: All persons employed by the company must complete a security awareness training course during employee orientation. Furthermore, each employee must take a security awareness refresher course at periodic intervals, not to exceed twelve months, as required by the department assigned with security-training responsibility.
Explanation/Notes: Many organizations disregard end-user awareness training altogether. According to the 2001 Global Information Security Survey, only 30 percent of the surveyed organizations spend money on awareness training for their user-community. Awareness training is an essential requirement to mitigate successful security breaches utilizing social engineering techniques.
4-18 Security training course for computer access Policy: Personnel must attend and successfully complete a security information course before being given access to any corporate computer systems. Explanation/Notes: Social engineers frequently target new employees, knowing that as a group they are generally the people least likely to be aware of the company's security policies and the proper procedures to determine classification and handling of sensitive information.
Training should include an opportunity for employees to ask questions about security policies. After training, the account holder should be required to sign a document acknowledging their understanding of the security policies, and their agreement to abide by the policies.
4-19 Employee badge must be color-coded
Policy: Identification badges must be color-coded to indicate whether the badge holder is an employee, contractor, temporary, vendor, consultant, visitor, or intern.
Explanation/Notes: The color of the badge is an excellent way to determine the status of a person from a distance. An alternative would be to use large lettering to indicate the badge holder's status, but using a color-coded scheme is unmistakable and easier to see.
A common social engineering tactic to gain access to a physical building is to dress up as a delivery person or repair technician. Once inside the facility, the attacker will masquerade as another employee or lie about his status to obtain cooperation from unsuspecting employees. The purpose of this policy is to prevent people from entering the building legitimately and then entering areas they should not have access to. For example, a person entering the facility as a telephone repair technician would not be able to masquerade as an employee: The color of the badge would give him away.
|
|||||||
|
Последнее изменение этой страницы: 2020-11-11; просмотров: 137; Нарушение авторского права страницы; Мы поможем в написании вашей работы! infopedia.su Все материалы представленные на сайте исключительно с целью ознакомления читателями и не преследуют коммерческих целей или нарушение авторских прав. Обратная связь - 3.128.199.175 (0.033 с.) |